The Illustrated Network- P54 pptx
Bạn đang xem bản rút gọn của tài liệu. Xem và tải ngay bản đầy đủ của tài liệu tại đây (457.67 KB, 10 trang )
> lnxserver
Server: 10.10.12.77
Address: 10.10.12.77#53
Non-authoritative answer:
Name: lnxserver.booklab.englab.jnpr.net
Address: 10.10.11.66
Simple DNS has a nice GUI, in contrast to the text fi les used in most Unix DNS
versions (as shown in Figure 19.4).
The Ethereal capture in Figure 19.5 shows the utter simplicity of the DNS message
exchanges. There’s even a nice log of these messages, as shown in Figure 19.6 (it also
tracks DHCP leases when dynamic DNS is used).
Now we can fi nally ping on the Illustrated Network the “normal” way.
[root@lnxclient admin]# ping wincli1.booklab.englab.jnpr.net
PING wincli1.booklab.englab.jnpr.net (10.10.11.51) 56(84) bytes of data.
6 4 bytes from wincli1.booklab.englab.jnpr.net (10.10.11.51): icmp_seq=1
ttl=126 time=0.768 ms
6 4 bytes from wincli1.booklab.englab.jnpr.net (10.10.11.51): icmp_seq=2
ttl=126 time=0.283 ms
FIGURE 19.4
DNS records on winsrv1 using a GUI. Note the various record types (the name servers in
particular).
CHAPTER 19 The Domain Name System 499
FIGURE 19.5
DNS server reply. Note that the question fi eld shows up as “queries.”
FIGURE 19.6
DNS server log showing the history of queries and responses.
500 PART IV Application Level
6 4 bytes from wincli1.booklab.englab.jnpr.net (10.10.11.51): icmp_seq=3
ttl=126 time=0.285 ms
6 4 bytes from wincli1.booklab.englab.jnpr.net (10.10.11.51): icmp_seq=4
ttl=126 time=0.259 ms
6 4 bytes from wincli1.booklab.englab.jnpr.net (10.10.11.51): icmp_seq=5
ttl=126 time=0.276 ms
6 4 bytes from wincli1.booklab.englab.jnpr.net (10.10.11.51): icmp_seq=6
ttl=126 time=0.244 ms
6 4 bytes from wincli1.booklab.englab.jnpr.net (10.10.11.51): icmp_seq=7
ttl=126 time=0.259 ms
^C
wincli1.booklab.englab.jnpr.net ping statistics
7 packets transmitted, 7 received, 0% packet loss, time 8080ms
rtt min/avg/max/mdev = 0.244/0.325/0.768/0.158 ms
[root@lnxclient admin]#
LAN1 is also running a DNS server on lnxserver, and to keep the confi guration
very simple only functions as a non-authoritative server. The confi guration is short and
sweet:
lnxserver$ cat /etc/named.conf
options {
directory "/var/named";
};
// this is a caching only name server zone configuration
zone "." {
type hint;
file "named.ca";
};
zone "0.0.127.in-addr.local";
type master;
file "named.local";
};
The two zone statements only point to the root servers on the Internet (in the hints fi le
named.ca) and make this server the master for its own loopback address. These two
zones appear in all name server confi gurations.
We should also limit the hosts from which recursion can be performed on the
caching name server. Otherwise, it might get used as a denial-of-service amplifi er. That
section would be:
allow-recursion { 127.0.0.1;
10.10.11.0/24;
};
We’ll point to the lnxserver name server on wincli1 on LAN1 and use nslookup to
verify that we can still fi nd the Internet name servers. At the interactive DNS prompt
(>), we’ll set the type of query to send to ns for name servers and we will look for “com.”
CHAPTER 19 The Domain Name System 501
This is the root of the entire “.com” Domain Name Space (note that we ask for com. and
not .com without the ending dot). Otherwise, the system would append a suffi x and try
to fi nd com.booklab.englab.jnpr.net and return an error (unless we did have a system
named “com” on the network).
> com.
Server: lnxserver.booklab.juniper.net
Address: 192.168.27.14
Non-authoritative answer:
com nameserver = f.gtld-servers.net
com nameserver = g.gtld-servers.net
com nameserver = h.gtld-servers.net
com nameserver = i.gtld-servers.net
com nameserver = j.gtld-servers.net
com nameserver = k.gtld-servers.net
com nameserver = l.gtld-servers.net
com nameserver = m.gtld-servers.net
com nameserver = a.gtld-servers.net
com nameserver = b.gtld-servers.net
com nameserver = c.gtld-servers.net
com nameserver = d.gtld-servers.net
com nameserver = e.gtld-servers.net
a.gtld-servers.net internet address = 192.5.6.30
a.gtld-servers.net AAAA IPv6 address = 2001:503:a83e::2:30
b.gtld-servers.net internet address = 192.33.14.30
b.gtld-servers.net AAAA IPv6 address = 2001:503:231d::2:30
c.gtld-servers.net internet address = 192.26.92.30
d.gtld-servers.net internet address = 192.31.80.30
e.gtld-servers.net internet address = 192.12.94.30
f.gtld-servers.net internet address = 192.35.51.30
g.gtld-servers.net internet address = 192.42.93.30
h.gtld-servers.net internet address = 192.54.112.30
i.gtld-servers.net internet address = 192.43.172.30
j.gtld-servers.net internet address = 192.48.79.30
k.gtld-servers.net internet address = 192.52.178.30
l.gtld-servers.net internet address = 192.41.162.30
m.gtld-servers.net internet address = 192.55.83.30
There are 13 servers, A through M, on the fi rst part of the list. But instead of being
called “root servers” these are “gltd servers.” GLTD stands for generic top-level domains
(sometimes seen as gTLD), and that’s what the traditional Internet host name endings
such as .com, .mil, .org, and so on are in DNS. There are also ccTLDs (country code
TLDs), such as .fr for France and .ca for Canada.
Note that the A and B GTLD servers return AAAA record types, showing that the
A6 and DNAME records (once so promising) are obsolete. We’re not supposed to use
nslookup (dig is not built into Windows XP, but can be installed as freeware). Let’s see
what dig can do, this time on the FreeBSD client.
502 PART IV Application Level
bsdclient# dig
; <<>> DiG 8.3 <<>>
;; res options: init recurs defnam dnsrch
;; got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 10624
;; flags: qr rd ra; QUERY: 1, ANSWER: 13, AUTHORITY: 0, ADDITIONAL: 13
;; QUERY SECTION:
;; ., type = NS, class = IN
;; ANSWER SECTION:
. 12h46m16s IN NS d.root-servers.net.
. 12h46m16s IN NS a.root-servers.net.
. 12h46m16s IN NS h.root-servers.net.
. 12h46m16s IN NS c.root-servers.net.
. 12h46m16s IN NS g.root-servers.net.
. 12h46m16s IN NS f.root-servers.net.
. 12h46m16s IN NS b.root-servers.net.
. 12h46m16s IN NS j.root-servers.net.
. 12h46m16s IN NS k.root-servers.net.
. 12h46m16s IN NS l.root-servers.net.
. 12h46m16s IN NS m.root-servers.net.
. 12h46m16s IN NS i.root-servers.net.
. 12h46m16s IN NS e.root-servers.net.
;; ADDITIONAL SECTION:
d.root-servers.net. 12h46m16s IN A 128.8.10.90
a.root-servers.net. 12h46m16s IN A 198.41.0.4
h.root-servers.net. 12h46m16s IN A 128.63.2.53
c.root-servers.net. 12h46m16s IN A 192.33.4.12
g.root-servers.net. 12h46m16s IN A 192.112.36.4
f.root-servers.net. 12h46m16s IN A 192.5.5.241
b.root-servers.net. 12h46m16s IN A 192.228.79.201
j.root-servers.net. 12h46m16s IN A 192.58.128.30
k.root-servers.net. 12h46m16s IN A 193.0.14.129
l.root-servers.net. 12h46m16s IN A 198.32.64.12
m.root-servers.net. 12h46m16s IN A 202.12.27.33
i.root-servers.net. 12h46m16s IN A 192.36.148.17
e.root-servers.net. 12h46m16s IN A 192.203.230.10
;; Total query time: 1 msec
;; FROM: bsdclient.booklab.englab.jnpr.net to SERVER: 10.10.11.66
;; WHEN: Fri Feb 22 10:10:00 2008
;; MSG SIZE sent: 17 rcvd: 449
bsdclient#
That’s a lot more detailed information, and it doesn’t use an interactive prompt.
By default, dig looks for root NS records and serves up fl ags, TTL information (in user-
friendly units), and so on. Let’s look at a more complete (or realistic) example and look
CHAPTER 19 The Domain Name System 503
for the IP address of the server for www.amazon.com (perhaps so you can prepare to
order more copies of this book).
bsdclient# dig www.amazon.com
; <<>> DiG 8.3 <<>> www.amazon.com
;; res options: init recurs defnam dnsrch
;; got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 10904
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0
;; QUERY SECTION:
;; www.amazon.com, type = A, class = IN
;; ANSWER SECTION:
www.amazon.com. 1m7s IN A 207.171.175.35
;; Total query time: 95 msec
;; FROM: bsdclient.booklab.englab.jnpr.net to SERVER: 10.10.11.66
;; WHEN: Fri Feb 22 10:40:17 2008
;; MSG SIZE sent: 32 rcvd: 48
dig
got us an answer, but not an authoritative one (AUTHORITY: 0). To get the author-
itative answer to the Amazon Web site, and not something from cache, we’ll have to fi nd
the Amazon name servers and ask one of them.
bsdclient# dig www.amazon.com ns
; <<>> DiG 8.3 <<>> www.amazon.com ns
;; res options: init recurs defnam dnsrch
;; got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 44598
;; flags: qr rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 1
;; QUERY SECTION:
;; www.amazon.com, type = NS, class = IN
;; ANSWER SECTION:
www.amazon.com. 21h7m55s IN NS ns-40.amazon.com.
www.amazon.com. 21h7m55s IN NS ns-30.amazon.com.
www.amazon.com. 21h7m55s IN NS ns-20.amazon.com.
www.amazon.com. 21h7m55s IN NS ns-10.amazon.com.
;; ADDITIONAL SECTION:
ns-40.amazon.com. 21h7m55s IN A 207.171.169.7
;; Total query time: 1 msec
;; FROM: bsdclient.booklab.englab.jnpr.net to SERVER: 10.10.11.66
;; WHEN: Fri Feb 22 10:38:37 2008
;; MSG SIZE sent: 32 rcvd: 128
Amazon has four name servers (note we found these answers cached, because of
the AUTHORITY: 0). We’ll ask ns-40 about Amazon’s Web site:
504 PART IV Application Level
bsdclient# dig @ns-40.amazon.com www.amazon.com A
; <<>> DiG 8.3 <<>> @ns-40.amazon.com www.amazon.com A
; (1 server found)
;; res options: init recurs defnam dnsrch
;; got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 6717
;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 0
;; QUERY SECTION:
;; www.amazon.com, type = A, class = IN
;; AUTHORITY SECTION:
www.amazon.com. 1m7s IN A 207.171.166.48
;; Total query time: 3 msec
;; FROM: bsdclient.booklab.englab.jnpr.net to SERVER: 204.74.101.1
;; WHEN: Fri Feb 22 10:32:52 2008
;; MSG SIZE sent: 32 rcvd: 112
Now AUTHORITY: 1 appears. It’s nice to know that Amazon’s own name server
is authoritative for itself. But let’s not get too worried about authoritative answers.
Cached information is usually just as good. In fact, look what happens when we repeat
the query.
bsdclient# dig @ns-40.amazon.com www.amazon.com A
; <<>> DiG 8.3 <<>> @ns-40.amazon.com www.amazon.com A
; (1 server found)
;; res options: init recurs defnam dnsrch
;; got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 52895
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0
;; QUERY SECTION:
;; www.amazon.com, type = A, class = IN
;; ANSWER SECTION:
www.amazon.com. 1m7s IN A 207.171.175.35
;; Total query time: 91 msec
;; FROM: bsdclient.booklab.englab.jnpr.net to SERVER: 207.171.169.7
;; WHEN: Fri Feb 22 10:55:29 2008
;; MSG SIZE sent: 32 rcvd: 48
Isn’t the ns-40 server still authoritative? Sure, but our earlier query just popped that
information into the local cache. Why fetch up an authoritative reply when there’s one
just as good in cache? Caching can be a nuisance when trying to “force” authoritative
answers, especially across the Internet.
Dig has been criticized for feature bloat. For comparison, the host DNS utility retains
the clean and sparse Unix output philosophy.
CHAPTER 19 The Domain Name System 505
bsdclient# host www.amazon.com
www.amazon.com has address 207.171.166.102
bsdclient#
Even at its most verbose, host is not as forthcoming as the other utilities.
bsdclient# host -v www.amazon.com ns-40.amazon.com
Using domain server:
Name: ns-40.amazon.com
Addresses: 207.171.169.7
Trying null domain
rcode = 0 (Success), ancount=1
The following answer is not verified as authentic by the server:
www.amazon.com 67 IN A 207.171.175.29
This has been by no means an exhaustive look at how DNS acts. For more informa-
tion, the excellent DNS and BIND by Cricket Liu (O’Reilly Media) should be consid-
ered defi nitive.
506 PART IV Application Level
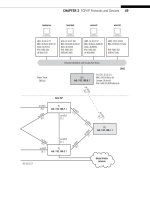
QUESTIONS FOR READERS
Figure 19.7 shows some of the concepts discussed in this chapter and can be used to
help you answer the following questions.
1. How many questions (queries) are usually present in a DNS request?
2. Is the message in the fi gure a query or a response?
3. What are the host names of the client and the DNS server on the Illustrated
Network that correspond to the IP addresses in the fi gure?
4. The fl ag fi eld value is
0x8580. Is the DNS server authoritative for the zone?
5. Based on the fl ag fi eld value, is recursion desired and available?
FIGURE 19.7
A DNS server reply message parsed by Ethereal.
507