Introducing Windows Azure- P38 pot
Bạn đang xem bản rút gọn của tài liệu. Xem và tải ngay bản đầy đủ của tài liệu tại đây (131.8 KB, 5 trang )
CHAPTER 5 ■ AZURE .NET SERVICES—ACCESS CONTROL
163
claim.Resource.ToString(),
"
claimValue))
{
if (AccessControlHelper.IsIssuedByIbn(claimSet))
{
return;
}
}
}
}
throw new FaultException("Access denied.");
}
static bool IsIssuedByIbn(ClaimSet claimSet)
{
foreach (Claim claim in claimSet.Issuer)
{
if (AccessControlHelper.CheckClaim(
claim.ClaimType,
claim.Resource.ToString(),
"
"accesscontrol.windows.net"))
{
return true;
}
}
return false;
}
static bool CheckClaim(string claimType, string claimValue,
string expectedClaimType, string expectedClaimValue)
{
if (
StringComparer.OrdinalIgnoreCase.Equals(claimType, expectedClaimType) &&
StringComparer.OrdinalIgnoreCase.Equals(claimValue, expectedClaimValue)
)
{
return true;
}
return false;
}
}
}
Now let's modify the WCF service operation implementation. For all implementations of the
operation in the WCF service contract we need to insert the code to demand the claim for the security
token by using the previous helper class as Listing 5-18 shows.
CHAPTER 5 ■ AZURE .NET SERVICES—ACCESS CONTROL
164
Listing 5-18. Implementation of the WCF Service Contract
using System;
using System.Runtime.Serialization;
using System.ServiceModel;
using System.ServiceModel.Channels;
using System.Collections.Generic;
using System.IO;
using System.Xml;
using System.Xml.Serialization;
using System.Text;
namespace AzureForDotNetDeveloper.DotNetService.ServiceBus
{
[ServiceBehavior(InstanceContextMode = InstanceContextMode.Single)]
public class AzureForDotNetDeveloperWCFservice : IAzureForDotNetDeveloperWCFservice
{
private User registeredUser = null;
#region IUserRegisterService Members
public string Ping()
{
AccessControlHelper.DemandActionClaim("UserRegister.Ping");
return string.Format(" I am here <{0}>", this.ToString());
}
public void RegisterUser(string xmlString)
{
try
{
AccessControlHelper.DemandActionClaim("UserRegister.RegisterUser");
XmlDocument xmlDoc = new XmlDocument();
xmlDoc.LoadXml(xmlString);
XmlSerializer serializer = new XmlSerializer(typeof(User));
StringReader reader = new StringReader(xmlString);
registeredUser = (User)serializer.Deserialize(reader);
}
catch (Exception ex)
{
}
}
public string GetRegisteredUser()
{
AccessControlHelper.DemandActionClaim("UserRegister.GetRegisteredUser");
XmlSerializer serializer = new XmlSerializer(typeof(User));
StringBuilder sb = new StringBuilder();
CHAPTER 5 ■ AZURE .NET SERVICES—ACCESS CONTROL
165
StringWriter writer = new StringWriter(sb);
serializer.Serialize(writer, registeredUser);
return writer.GetStringBuilder().ToString();
}
#endregion
}
}
Finally, update the service reference on the client project. Start running the service, and go to Visual
Studio. Right-click on the Service Reference node to update the client proxy class. The App.config file is
also going to be regenerated by Visual Studio to reflect the security access information with binding type
ws2007FederationHttpBinding as Listing 5-19 shows.
Listing 5-19. Generated Client Proxy Configuration with Security Access Claim Token Encoding
<ws2007FederationHttpBinding>
<binding name="UserRegisterEndpoint1" closeTimeout="00:01:00"
openTimeout="00:01:00" receiveTimeout="00:10:00" sendTimeout="00:01:00"
bypassProxyOnLocal="false" transactionFlow="false"
hostNameComparisonMode="StrongWildcard"
maxBufferPoolSize="524288" maxReceivedMessageSize="65536" messageEncoding="Text"
textEncoding="utf-8" useDefaultWebProxy="true">
<readerQuotas maxDepth="32" maxStringContentLength="8192" maxArrayLength="16384"
maxBytesPerRead="4096" maxNameTableCharCount="16384" />
<reliableSession ordered="true" inactivityTimeout="00:10:00"
enabled="false" />
<security mode="Message">
<message algorithmSuite="Default" issuedKeyType="SymmetricKey"
issuedTokenType="
negotiateServiceCredential="false">
<issuer
address=
" for certificate"
binding="customBinding"
bindingConfiguration=
" for certificate">
<identity>
<certificate
encodedValue="AwAAAAEAAAAUAAAAQW5vpdmCsJaTH79CxKPc1giFbJUgAAAAAQAAADMGAAAwggYvM
IIFF6ADAgECAgowSxUCAAUAAN+/MA0GCSqGSIb3DQEBBQUAMIGLMRMwEQYKCZImiZPyLGQBGRYDY29tMRkwFwYKCZImi
ZPyLGQBGRYJbWljcm9zb2Z0MRQwEgYKCZImiZPyLGQBGRYEY29ycDEXMBUGCgmSJomT8ixkARkWB3JlZG1vbmQxKjAoB
gNVBAMTIU1pY3Jvc29mdCBTZWN1cmUgU2VydmVyIEF1dGhvcml0eTAeFw0wODA5MDQyMDExMDJaFw0wOTA5MDQyMDExM
DJaMH0xCzAJBgNVBAYTAlVTMQswCQYDVQQIEwJXQTEQMA4GA1UEBxMHUmVkbW9uZDESMBAGA1UEChMJTWljcm9zb2Z0M
RcwFQYDVQQLEw5Qcm9qZWN0IFp1cmljaDEiMCAGA1UEAxMZYWNjZXNzY29udHJvbC53aW5kb3dzLm5ldDCBnzANBgkqh
kiG9w0BAQEFAAOBjQAwgYkCgYEAreESUDU/HSaVXHmBHfBdUZW7yLlvFRiB+GX/gIEz94H6HW85Doo+0gT8GEORtite+
oREcom6euSUYarP3Rt/1rIvtJAU/+GhcupKvICZAavx9vPLrfjxgayHuSCc8QbAOnpn44f/LE37q+Y22g8uqOg3aQE7J
CHAPTER 5 ■ AZURE .NET SERVICES—ACCESS CONTROL
166
Olb0wW//+2yXScCAwEAAaOCAyQwggMgMAsGA1UdDwQEAwIEsDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwe
AYJKoZIhvcNAQkPBGswaTAOBggqhkiG9w0DAgICAIAwDgYIKoZIhvcNAwQCAgCAMAsGCWCGSAFlAwQBKjALBglghkgBZ
QMEAS0wCwYJYIZIAWUDBAECMAsGCWCGSAFlAwQBBTAHBgUrDgMCBzAKBggqhkiG9w0DBzAdBgNVHQ4EFgQUaqPI5cP+U
HaMNfk5i8kWU3mza84wHwYDVR0jBBgwFoAUFFXEOeA9LtFVLkiWsNh+FCIGk7wwggEKBgNVHR8EggEBMIH+MIH7oIH4o
IH1hlhodHRwOi8vbXNjcmwubWljcm9zb2Z0LmNvbS9wa2kvbXNjb3JwL2NybC9NaWNyb3NvZnQlMjBTZWN1cmUlMjBTZ
XJ2ZXIlMjBBdXRob3JpdHkoNSkuY3JshlZodHRwOi8vY3JsLm1pY3Jvc29mdC5jb20vcGtpL21zY29ycC9jcmwvTWljc
m9zb2Z0JTIwU2VjdXJlJTIwU2VydmVyJTIwQXV0aG9yaXR5KDUpLmNybIZBaHR0cDovL2NvcnBwa2kvY3JsL01pY3Jvc
29mdCUyMFNlY3VyZSUyMFNlcnZlciUyMEF1dGhvcml0eSg1KS5jcmwwgb8GCCsGAQUFBwEBBIGyMIGvMF4GCCsGAQUFB
zAChlJodHRwOi8vd3d3Lm1pY3Jvc29mdC5jb20vcGtpL21zY29ycC9NaWNyb3NvZnQlMjBTZWN1cmUlMjBTZXJ2ZXIlM
jBBdXRob3JpdHkoNSkuY3J0ME0GCCsGAQUFBzAChkFodHRwOi8vY29ycHBraS9haWEvTWljcm9zb2Z0JTIwU2VjdXJlJ
TIwU2VydmVyJTIwQXV0aG9yaXR5KDUpLmNydDA/BgkrBgEEAYI3FQcEMjAwBigrBgEEAYI3FQiDz4lNrfIChaGfDIL6y
n2B4ft0gU+Dwu2FCI6p0oVjAgFkAgEGMCcGCSsGAQQBgjcVCgQaMBgwCgYIKwYBBQUHAwIwCgYIKwYBBQUHAwEwDQYJK
oZIhvcNAQEFBQADggEBAB3JqyYxQ80PLVFMRoE2chN0+QlA8oijsPNkEz0ycysiyQQ3zpDgJxqa2IgULzFvuKB7C1FlD
SM5U6tWQcKKeJQ2sqAreR1mYec1JIpJQZG6KZDAQHqe2Rvhg54kD8MZeJCbd7Rkxl2E5ivekhbxZhKoNnsC0pEN2rEoQ
urCSkzDQ1eTNp3PaiHds+6iVNsg+u8aIXkWqn7/mj9x6UJQe0vXGhy/h/tBJLrCXzBl8gDdG7ie5VNC1LzW6gjukQEJf
mlEZTWW/EnMhj7cubG7/VHjk/2rvjbJS2pjxojRwyqLwyRHfSMpTP92pJ7REu91d1jReylDFdn58PfA3eYOoik=" />
</identity>
</issuer>
<issuerMetadata
address="
<identity>
<dns value="accesscontrol.windows.net" />
</identity>
</issuerMetadata>
<tokenRequestParameters>
<trust:SecondaryParameters
xmlns:trust="
<trust:TokenType
xmlns:trust="
</trust:TokenType>
<trust:KeyType
xmlns:trust="
</trust:KeyType>
<trust:KeySize
xmlns:trust="
256
</trust:KeySize>
<trust:Claims Dialect="
xmlns:trust="
<wsid:ClaimType
Uri="
xmlns:wsid=" />
</trust:Claims>
<trust:KeyWrapAlgorithm
xmlns:trust="
</trust:KeyWrapAlgorithm>
<trust:EncryptWith
xmlns:trust="
CHAPTER 5 ■ AZURE .NET SERVICES—ACCESS CONTROL
167
</trust:EncryptWith>
<trust:SignWith
xmlns:trust="
</trust:SignWith>
<trust:CanonicalizationAlgorithm
xmlns:trust="
</trust:CanonicalizationAlgorithm>
<trust:EncryptionAlgorithm
xmlns:trust="
</trust:EncryptionAlgorithm>
</trust:SecondaryParameters>
</tokenRequestParameters>
</message>
</security>
</binding>
</ws2007FederationHttpBinding>
</bindings>
<client>
<endpoint address="http://localhost/AzureForDotNetDeveloperWCFservice"
binding="basicHttpBinding" bindingConfiguration="UserRegisterEndpoint"
contract="UserRegister" name="UserRegisterEndpoint" />
<endpoint address="http://localhost/AzureForDotNetDeveloperWCFservice"
binding="ws2007FederationHttpBinding" bindingConfiguration="UserRegisterEndpoint1"
contract="UserRegisterService.UserRegisterService" name="UserRegisterEndpoint1">
<identity>
<certificate encodedValue="AwAAAAEAAAAUAAAAASCQin4SUkWbN0uSZBQY6A0SY/wgAAAAAQAAALU
BAAAwggGxMIIBX6ADAgECAhDvE+ZAuwIqhU9cQqsE44DOMAkGBSsOAwIdBQAwFjEUMBIGA1UEAxMLUm9vdCBBZ2VuY3k
wHhcNMDcwNDA0MjMyMTAxWhcNMzkxMjMxMjM1OTU5WjAUMRIwEAYDVQQDEwlsb2NhbGhvc3QwgZ8wDQYJKoZIhvcNAQE
BBQADgY0AMIGJAoGBAK3fOF9Q789iQiEs5FpNTOLOnraBTcoNMxK+jFasM+S8FMLSqPGRgrKearjGwAum3diRBKOngDj
bJ+Vp8TxtgvhEhed9JBuWh5hg6nk0jVS7emHjwkBoacULtYTo4QC2/Bav/eK6ibO/kSknnVG45v7kNWG2gyJh+/HCJIc
xQ3oFAgMBAAGjSzBJMEcGA1UdAQRAMD6AEBLkCS0GHR1PAI1hIdwWZGOhGDAWMRQwEgYDVQQDEwtSb290IEFnZW5jeYI
QBjdsAKoAZIoRz7jUqlw19DAJBgUrDgMCHQUAA0EAdZ/POL0NGuxU3kAoTsbSPdvi3k5PhAYLYbIL2RRHxjcV5lPHqK9
BP2QoctoRFt1Kqb30ZSrGXH5oaq3B/Vdpdg==" />
</identity>
</endpoint>
</client>
</system.serviceModel>
</configuration>
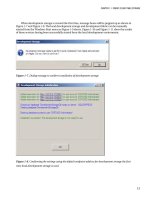
Start the server and enter the Azure solution name. The server will retrieve the certificate
information from the system as Figure 5-18 shows.