Chương 1
Bạn đang xem bản rút gọn của tài liệu. Xem và tải ngay bản đầy đủ của tài liệu tại đây (10.77 MB, 192 trang )
<span class="text_page_counter">Trang 1</span><div class="page_container" data-page="1">
<b>Chương 1: Tổng quan về mô hình truyền thơng</b>
<small></small>
<b>Nguyễn Thanh Đăng, bài giảng Mạng và Truyền dữ liệu, ÐHCN Tp.HCM, 2016.</b>
</div><span class="text_page_counter">Trang 2</span><div class="page_container" data-page="2"><b>Chương 1: </b>
<b>Tổng quan về mơ hình truyền thơng</b>
</div><span class="text_page_counter">Trang 3</span><div class="page_container" data-page="3"><b>1.1 Các thành phần chính của mạng máy tính.</b>
<b>n</b>
</div><span class="text_page_counter">Trang 4</span><div class="page_container" data-page="4"><b>1.1 Các thành phần chính của mạng máy tính.</b>
<b>n</b>
</div><span class="text_page_counter">Trang 6</span><div class="page_container" data-page="6"><b>1.2 Mơ hình OSI.</b>
<small></small> <b>Các cơng việc liên quan q trình gửi 1 bức thư</b>
</div><span class="text_page_counter">Trang 7</span><div class="page_container" data-page="7"><b>1.2 Mơ hình OSI.</b>
<small></small> <b>n</b>
</div><span class="text_page_counter">Trang 8</span><div class="page_container" data-page="8"><b>1.2 Mơ hình OSI.</b>
<small></small> <b>n</b>
</div><span class="text_page_counter">Trang 9</span><div class="page_container" data-page="9"><b>1.2 Mơ hình OSI.</b>
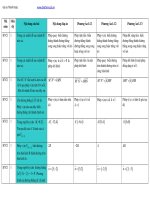
<small></small> <b>Mơ hình OSI 7 lớp: gồm 7 lớp riêng biệt nhưng có liên hệ với nhau, mỗi lớp nhằm định nghĩa một phân đoạn trong quá trình di chuyển thông tin qua mạng.</b>
</div><span class="text_page_counter">Trang 10</span><div class="page_container" data-page="10"><b>1.2 Mơ hình OSI.</b>
<small></small> <b>Chức năng mỗi lớp trong mơ hình OSI:</b>
<i><b><small>a)</small>Lớp vật lý (Physical layer):</b></i><b>Lớp vật lý chịu trách </b>
<b>nhiệm cho việc di chuyển các bit riêng lẻ từ 1 hop </b>
<b>(nút) đến nút kế tiếp. Lớp này liên quan đến các đặc tính cơ, điện của giao diện thiết bị và môi trường </b>
<b>truyền.</b>
</div><span class="text_page_counter">Trang 11</span><div class="page_container" data-page="11"><b>1.2 Mô hình OSI.</b>
</div><span class="text_page_counter">Trang 13</span><div class="page_container" data-page="13"><b>1.2 Mơ hình OSI.</b>
<b><small>b)Lớp liên kết dữ liệu (Data link layer): </small>Lớp liên kết dữ liệu chịu trách nhiệm chuyển các frame từ 1 hop (nút) đến hop khác.</b>
</div><span class="text_page_counter">Trang 14</span><div class="page_container" data-page="14"><b>1.2 Mơ hình OSI.</b>
<small></small> <b><small>Nhiệm vụ</small></b>
<small></small> <b><small>Break L3 (Network) data into reasonable size (Frame)</small></b>
<small></small> <b><small>Truyền khung/frame từ nút đến nút trong một mạng</small></b>
<small></small> <b><small>Guarantee Node-to-Node delivery (Frame Error Free)</small></b>
<small></small> <b><small>Service</small></b>
<small></small> <b><small>Tạo khung (thêm header & trailer)</small></b>
<small></small> <b><small>Định địa chỉ vật lý (MAC address: 12 digit hexadecimal (e.g. 080BF0AFDC09))</small></b>
<small></small> <b><small>Same sender network:source & destination address</small></b>
<small></small> <b><small>Outside sender network: source & connecting devices (bridge, router, gateway) address</small></b>
<small></small> <b><small>Điều khiển lưu lượng:frame acknowledgement, inform buffer size, etc.</small></b>
<small></small> <b><small>Kiểm soát lỗi:error detection and error correction</small></b>
<small></small> <b><small>Điều khiển truy cập: checking accessibility (ex. Multipoint connection)</small></b>
</div><span class="text_page_counter">Trang 15</span><div class="page_container" data-page="15"><b>1.2 Mơ hình OSI.</b>
<small></small> <b>Phân phối hop đến hop</b>
</div><span class="text_page_counter">Trang 16</span><div class="page_container" data-page="16"><b>1.2 Mơ hình OSI.</b>
<b><small>c) Lớp mạng (Network layer): </small>Lớp mạng chịu trách nhiệm phân phối các gói tin riêng rẽ từ host nguồn đến host đích.</b>
</div><span class="text_page_counter">Trang 17</span><div class="page_container" data-page="17"><small></small> <b><small>Logical (Network) address (header):IP address</small></b>
<small></small> <b><small>Định tuyến các gói tin đi qua thiết bị liên mạng</small></b>
<small></small> <b><small>Router || Gateway</small></b>
</div><span class="text_page_counter">Trang 18</span><div class="page_container" data-page="18"><b>1.2 Mơ hình OSI.</b>
<small></small> <b>Phân phối từ nguồn đến đích</b>
</div><span class="text_page_counter">Trang 19</span><div class="page_container" data-page="19"><b>1.2 Mơ hình OSI.</b>
<b><small>d)Lớp giao vận (Transport layer): </small>Lớp giao vận chịu trách nhiệm phân phối message từ một quá </b>
<b>trình/process đến quá trình khác.</b>
</div><span class="text_page_counter">Trang 20</span><div class="page_container" data-page="20"><b>1.2 Mơ hình OSI.</b>
<small></small> <b><small>Nhiệm vụ</small></b>
<small></small> <b><small>Đảm bảo phân phối toàn bộ từ nguồn đến đích cuối cùng</small></b>
<small></small> <b><small>Service</small></b>
<small></small> <b><small>Service-point addressing:Port address (16 bits: 0 – 65,535 ports)</small></b>
<small></small> <b><small>Each application is assigned a specific port address</small></b>
<small></small> <b><small>Segmentation and Reassembly</small></b>
<small></small> <b><small>Source:segment L5 data into small segments</small></b>
<small></small> <b><small>Destination:reassembly small segments into a whole message</small></b>
<small></small> <b><small>Điều khiển kết nối</small></b>
<small></small> <b><small>Khơng kết nối/Connectionless</small></b>
<small></small> <b><small>Hướng kết nối/Connection-oriented</small></b>
<small></small> <b><small>Kiểm sốt lỗi: dị và sửa sai tồn bộ message</small></b>
<small></small> <b><small>Điều khiển luồng</small></b>
</div><span class="text_page_counter">Trang 21</span><div class="page_container" data-page="21"><b>1.2 Mơ hình OSI.</b>
<b><small>e)Lớp phiên (Session layer): Lớp phiên chịu trách nhiệm điều khiển và đồng bộ dialog.</small></b>
</div><span class="text_page_counter">Trang 22</span><div class="page_container" data-page="22"><small></small> <b><small>Traffic control & direction control</small></b>
<small></small> <b><small>Đồng bộ thông điệp/Message synchronization</small></b>
<small></small> <b><small>Adding checkpoints (synchronization points) in the message stream</small></b>
</div><span class="text_page_counter">Trang 23</span><div class="page_container" data-page="23"><b>1.2 Mơ hình OSI.</b>
<b><small>f) Lớp trình diễn (Presentation layer): </small>Lớp trình diễn chịu trách nhiệm biên dịch, nén và mã hóa</b>
</div><span class="text_page_counter">Trang 24</span><div class="page_container" data-page="24"><small></small> <b><small>Ex. ASCII -> non ASCII system</small></b>
<small></small> <b><small>Mã hóa (privacy & security)</small></b>
<small></small> <b><small>Đối với các thông tin nhạy cảm: login-password, thẻ tín dung, tài khoản ngân hàng, thơng tin cá nhân</small></b>
<small></small> <b><small>Nén</small></b>
<small></small> <b><small>Ex. Zip, Gif, JPEG</small></b>
</div><span class="text_page_counter">Trang 25</span><div class="page_container" data-page="25"><b>1.2 Mơ hình OSI.</b>
<b><small>g) Lớp ứng dụng (Application layer): </small>Lớp ứng dụng chịu trách nhiệm cung cấp các dịch vụ đến người sử dụng. </b>
</div><span class="text_page_counter">Trang 26</span><div class="page_container" data-page="26"><small></small> <b><small>Network Virtual Terminal</small></b>
<small></small> <b><small>Truyền , truy xuất và quản lý file/File transfer, access, and management (FTAM)</small></b>
<small></small> <b><small>Dịch vụ mail</small></b>
<small></small> <b><small>Truy cập WWW</small></b>
</div><span class="text_page_counter">Trang 27</span><div class="page_container" data-page="27"><b>1.2 Mơ hình OSI.</b>
<small></small> <b>Giao tiếp giữa các lớp trong mơ hình OSI </b>
</div><span class="text_page_counter">Trang 28</span><div class="page_container" data-page="28"><b>1.2 Mơ hình OSI.</b>
<small></small> <b>Trao đổi dữ liệu sử dụng mơ hình OSI</b>
</div><span class="text_page_counter">Trang 29</span><div class="page_container" data-page="29"><b>1.3 Mơ hình TCP/IP</b>
<small></small>
<b>The layers in theTCP/IP protocol suitedo not exactlymatch those in the OSI model. The original TCP/IPprotocol suite was defined as having four layers:host-to-network,internet,transport, andapplication.However, when TCP/IP is compared to OSI, we cansay that the TCP/IP protocol suite is made of fivelayers:physical,data link,network,transport, and</b>
<b>application.</b>
</div><span class="text_page_counter">Trang 30</span><div class="page_container" data-page="30"><b>1.3 Mơ hình TCP/IP</b>
</div><span class="text_page_counter">Trang 31</span><div class="page_container" data-page="31"><b>1.3 Mơ hình TCP/IP</b>
<small>Network Access</small>
</div><span class="text_page_counter">Trang 32</span><div class="page_container" data-page="32"><b>1.3 Mơ hình TCP/IP</b>
<b>a) Physical and Data Link Layers: </b>
At the physical and data link layers, TCP/IP does not define any specific protocol. It supports all the standard and proprietary protocols. A network in a TCP/IP
internetwork can be a local-area network or a wide-area network
<b>b) Network Layer<small>:</small></b>
At the network layer (or, more accurately, the
internetwork layer), TCP/IP supports the Internetworking Protocol. lP, in turn, uses four supporting protocols:
ARP, RARP, ICMP, and IGMP.
</div><span class="text_page_counter">Trang 33</span><div class="page_container" data-page="33"><b>1.3 Mơ hình TCP/IP</b>
<b><small>c) </small></b>Transport Layer:
Traditionally the transport layer was represented in
TCP/IP by two protocols· TCP and UDP. IP is a host protocol, meaning that it can deliver a packet from one physical device to another. UDP and TCP are
host-to-transport level protocols responsible for delivery of a message from a process (running program) to another process. A new transport layer protocol, SCTP, has been devised to meet the needs of some newer applications.
</div><span class="text_page_counter">Trang 34</span><div class="page_container" data-page="34"><b>1.3 Mô hình TCP/IP</b>
<b><small>h</small></b>
</div><span class="text_page_counter">Trang 35</span><div class="page_container" data-page="35"><b>1.3 Mơ hình TCP/IP</b>
<small></small> <b><small>UDP protocol:</small></b>
The User Datagram Protocol (UDP) is called a
connectionless, unreliable transport protocol. It does not add anything to the services of lP except to
provide process-toprocess communication instead of host-to-host communication. Also, it performs very limited error checking.
</div><span class="text_page_counter">Trang 36</span><div class="page_container" data-page="36"> Provides limited error checking
Provides best-effort delivery
Has no data-recovery features
<b>UDP Characteristics</b>
</div><span class="text_page_counter">Trang 37</span><div class="page_container" data-page="37"><b>1.3 Mơ hình TCP/IP</b>
<small></small> Well-Known Ports for UDP
</div><span class="text_page_counter">Trang 38</span><div class="page_container" data-page="38"><b>1.3 Mô hình TCP/IP</b>
Well-Known Ports for UDP
</div><span class="text_page_counter">Trang 40</span><div class="page_container" data-page="40"><b>1.3 Mơ hình TCP/IP</b>
<small></small> Checksum
<b>-The UDP checksum includes three sections: a </b>
pseudoheader, the UDP header, and the data coming from the application layer.
<b>-The pseudoheader is the part of the header of the lP </b>
packet in which the user datagram is to be encapsulated with some fields filled with Os
</div><span class="text_page_counter">Trang 41</span><div class="page_container" data-page="41"><b>1.3 Mơ hình TCP/IP</b>
<i><b><small>Pseudoheader for checksum calculation</small></b></i>
</div><span class="text_page_counter">Trang 42</span><div class="page_container" data-page="42"><b>1.3 Mơ hình TCP/IP</b>
<i>Example 23.2</i>
Figure 23.11 shows the checksum calculation for a very small user datagram with only 7 bytes of data. Because the number of bytes of data is odd, padding is added for checksum calculation. The pseudoheader as well as the padding will be dropped when the user datagram is
delivered to lP.
</div><span class="text_page_counter">Trang 43</span><div class="page_container" data-page="43"><b>1.3 Mô hình TCP/IP</b>
<small></small> User
</div><span class="text_page_counter">Trang 44</span><div class="page_container" data-page="44"><b>1.3 Mơ hình TCP/IP</b>
<small></small> UDP Operation
<i><b>-Connectionless Services: each user datagram sent by </b></i>
UDP is an independent datagram. There is no connection establishment and no connection termination
<i>-Flow and Error Control:UDP is a very simple, </i>
unreliable transport protocol. There is no flow control and hence no window mechanism. The receiver may overflow with incoming messages <small>44</small>
</div><span class="text_page_counter">Trang 45</span><div class="page_container" data-page="45"><b>1.3 Mơ hình TCP/IP</b>
<b><small>-</small></b><i>Encapsulation and Decapsulation: To send a message </i>
from one process to another, the UDP protocol encapsulates and decapsulates messages in an lP datagram.
<b><small>-</small></b><i>Queuing:</i>
</div><span class="text_page_counter">Trang 46</span><div class="page_container" data-page="46"><b>1.3 Mơ hình TCP/IP</b>
<small></small> <b><small>Use of UDP:</small></b>
<small>- UDP is suitable for a process that requires simple response communication with little concern for flow and error control. It is not usually used for a process such as FfP that needs to send bulk data.</small>
<small>request--UDP is suitable for a process with internal flow and error control mechanisms. For example, the Trivial File Transfer </small>
<small>Ptotocol (TFTP) process includes flow and error control. It can easily use UDP.</small>
</div><span class="text_page_counter">Trang 47</span><div class="page_container" data-page="47"><b>1.3 Mơ hình TCP/IP</b>
<small>- UDP is a suitable transport protocol for multicasting. </small>
<small>Multicasting capability is embedded in the UDP software but not in the TCP software.</small>
<small>- UDP is used for management processes.</small>
<small>- UDP is used for some route updating protocols such as Routing Information Protocol (RIP) </small>
</div><span class="text_page_counter">Trang 48</span><div class="page_container" data-page="48"><b>1.3 Mơ hình TCP/IP</b>
<small></small> <b><small>TCP (</small></b>Transmission Control Protocol) <b><small>protocol:</small></b> TCP is a connection-oriented protocol; it creates a virtual connection between two TCPs to send data. In
addition, TCP uses flow and error control mechanisms at the transport level. Therefore, TCP is called a
<i>connection-oriented, reliable transport protocol. It </i>
adds connection-oriented and reliability features to the services of lP
</div><span class="text_page_counter">Trang 49</span><div class="page_container" data-page="49"><b>1.3 Mơ hình TCP/IPTCP Characteristics</b>
<small></small> <b>Transport layer of the TCP/IP stack</b>
<small></small> <b>Access to the network layer for applications</b>
</div><span class="text_page_counter">Trang 50</span><div class="page_container" data-page="50"><b>1.3 Mơ hình TCP/IP</b>
<small></small> <b>TCP Services</b>
<small></small> <i>Process-to-Process Communication: Like UDP, TCP </i>
provides process-to-process communication using port numbers
</div><span class="text_page_counter">Trang 51</span><div class="page_container" data-page="51"><b>1.3 Mơ hình TCP/IP</b>
<i><b>Well-known ports used by TCP</b></i>
</div><span class="text_page_counter">Trang 52</span><div class="page_container" data-page="52"><b>1.3 Mơ hình TCP/IP</b>
<small></small> <i>Stream Delivery Service: TCP, unlike UDP, is a </i>
stream-oriented protocol. TCP allows the sending
process to deliver data as a stream of bytes and allows the receiving process to obtain data as a stream of
bytes. TCP creates an environment in which the two processes seem to be connected by an imaginary
"tube“ that carries their data across the Internet
</div><span class="text_page_counter">Trang 53</span><div class="page_container" data-page="53"><b>1.3 Mơ hình TCP/IP</b>
<i><b>Stream delivery</b></i>
</div><span class="text_page_counter">Trang 54</span><div class="page_container" data-page="54"><b>1.3 Mơ hình TCP/IP</b>
<small></small> <b>Sending and Receiving Buffers: Because the </b>
sending and the receiving processes may not write or read data at the same speed, TCP needs buffers for
storage. There are two buffers, the sending buffer and the receiving buffer, one for each direction
</div><span class="text_page_counter">Trang 55</span><div class="page_container" data-page="55"><b>1.3 Mơ hình TCP/IP</b>
<i><b>Sending and receiving buffers</b></i>
</div><span class="text_page_counter">Trang 56</span><div class="page_container" data-page="56"><small>datagrams and transmitted. This entire operation is transparent to the receiving process</small>
</div><span class="text_page_counter">Trang 57</span><div class="page_container" data-page="57"><b>1.3 Mơ hình TCP/IP</b>
<i><b>TCP segments</b></i>
</div><span class="text_page_counter">Trang 58</span><div class="page_container" data-page="58"><b>1.3 Mơ hình TCP/IP</b>
<small></small> <i><b>Full-Duplex Communication: TCP offers full-duplex </b></i>
service, in which data can flow in both directions at the same time. Each TCP then has a sending and
receiving buffer, and segments move in both directions.
</div><span class="text_page_counter">Trang 60</span><div class="page_container" data-page="60"><b>1.3 Mô hình TCP/IP</b>
<small></small> <i>Reliable Service: TCP is a reliable transport protocol. </i>
It uses an acknowledgment mechanism to checkthe safe and sound arrival of data
<small></small> 'I'CP Features
<small></small> <i>Numbering System: </i>
<i>-Byte Number: The bytes of data being transferred in </i>
each connection are numbered by TCP. The numbering starts with a randomly generated number. <sup>60</sup>
</div><span class="text_page_counter">Trang 61</span><div class="page_container" data-page="61"><b>1.3 Mơ hình TCP/IP</b>
<b>-Sequence Number: The value in the sequence number </b>
field of a segment defines the number of the first data byte contained in that segment
<b><small>-</small></b>Acknowledgment Number: The value of the
acknowledgment field in a segment defines the number of the next byte a party expects to receive. The
acknowledgment number is cumulative
</div><span class="text_page_counter">Trang 62</span><div class="page_container" data-page="62"><b>1.3 Mơ hình TCP/IP</b>
<small></small> <i><b>Flow Control : The receiver of the data controls the </b></i>
amount of data that are to be sent by the sender. This is done to prevent the receiver from being
overwhelmed with data. The numbering system allows TCP to use a byte-oriented flow control
<small></small> <i>Error Control</i>
<small></small> <i>Congestion Control</i>
</div><span class="text_page_counter">Trang 63</span><div class="page_container" data-page="63"><b>1.3 Mơ hình TCP/IP</b>
<small></small> Segment
<small></small> <i>Format</i><b><small>:</small></b>
</div><span class="text_page_counter">Trang 64</span><div class="page_container" data-page="64"><b>1.3 Mơ hình TCP/IP</b>
<i><b>Control field</b></i>
</div><span class="text_page_counter">Trang 65</span><div class="page_container" data-page="65"><b>1.3 Mơ hình TCP/IP</b>
<small></small> <b>A TCP Connection</b>
<small></small> <i>Connection Establishment</i><b><small>: </small></b>TCP transmits data in full-duplex mode. When two TCPs in two machines are connected, they are able to send segments to each other simultaneously. This implies that each party
must initialize connnunication and get approval from the other party before any data are transferred
</div><span class="text_page_counter">Trang 66</span><div class="page_container" data-page="66"><b>1.3 Mơ hình TCP/IP</b>
<b>Establishing a Connection</b>
</div><span class="text_page_counter">Trang 67</span><div class="page_container" data-page="67"><b>1.3 Mơ hình TCP/IP</b>
<b>-Three Way Handshaking: The connection establishment in TCP is called three way handshaking </b>
</div><span class="text_page_counter">Trang 69</span><div class="page_container" data-page="69"><b>1.3 Mô hình TCP/IP</b>
<small></small> <i>Data Transfer</i>
</div><span class="text_page_counter">Trang 70</span><div class="page_container" data-page="70"><b>1.3 Mơ hình TCP/IP</b>
<small></small> <i>Connection Termination</i>
<i><small>Connection termination using three-way handshaking</small></i>
</div><span class="text_page_counter">Trang 72</span><div class="page_container" data-page="72"><b>1.3 Mơ hình TCP/IP</b>
<small></small> <b>Flow Control: TCP uses a sliding window to handle </b>
flow control. The sliding window protocol used by TCP, however, is something between the Go-Back-Nand Selective Repeat sliding window.
</div><span class="text_page_counter">Trang 73</span><div class="page_container" data-page="73"><b>1.3 Mơ hình TCP/IP</b>
<b>Flow Control</b>
</div><span class="text_page_counter">Trang 74</span><div class="page_container" data-page="74"><b>1.3 Mơ hình TCP/IPTCP Acknowledgment</b>
</div><span class="text_page_counter">Trang 75</span><div class="page_container" data-page="75"><b>1.3 Mơ hình TCP/IPFixed Windowing</b>
</div><span class="text_page_counter">Trang 76</span><div class="page_container" data-page="76"><b>1.3 Mơ hình TCP/IP</b>
<i><b>Sliding window: A sliding window is used to make </b></i>
transmission more efficient as well as to control the flow of data so that the destination does not become
overwhelmed with data. TCP sliding windows are byte oriented
</div><span class="text_page_counter">Trang 77</span><div class="page_container" data-page="77"><b>1.3 Mơ hình TCP/IP</b>
<b>TCP Sliding Windowing</b>
</div><span class="text_page_counter">Trang 78</span><div class="page_container" data-page="78"><b>1.3 Mơ hình TCP/IP</b>
<small>Some points about TCP sliding windows:</small>
<i><small>-The size of the window is the lesser of rwnd and cwnd.</small></i>
<small>-The source does not have to send a full window's worth of data.-The wmdow can be opened or closed by the receiver, but shouW not be shrunk.</small>
<small>-The destination can send an acknowledgment at any time as long as it does not result in a shrinking window.</small>
<small>- The receiver can temporarily shut down the window; the sender, however, can always send a segment of 1 byte after the window is shut down</small>
<small>78</small>
</div><span class="text_page_counter">Trang 79</span><div class="page_container" data-page="79"><i>What is the value of the receiver window (rwnd) for host Aif the receiver, host B, has a buffer size of 5000 bytes and1000 bytes of received and unprocessed data?</i>
<i>Example 23.4</i>
<i>The value of rwnd = 5000 − 1000 = 4000. Host B canreceive only 4000 bytes of data before overflowing itsbuffer. Host B advertises this value in its next segment to A.</i>
</div><span class="text_page_counter">Trang 80</span><div class="page_container" data-page="80"><b>1.3 Mơ hình TCP/IP</b>
<b>TCP Sequence and Acknowledgment Numbers</b>
</div><span class="text_page_counter">Trang 81</span><div class="page_container" data-page="81"><b>1.3 Mơ hình TCP/IP</b>
<small></small> <b>Error Control</b>
<small></small> <i><b>Checksum:</b></i>
<b>-Each segment includes a checksum field which is used </b>
to check for a corrupted segment. If the segment is
corrupted, it is discarded by the destination TCP and is considered as lost
<b>-TCP uses a 16-bit checksum that is mandatory in every </b>
</div><span class="text_page_counter">Trang 82</span><div class="page_container" data-page="82"><b>1.3 Mơ hình TCP/IP</b>
<small></small> <i><b>Acknowledgment: TCP uses acknowledgments to </b></i>
confirm the receipt of data segments. Control segments that carry no data but consume a sequence number are also acknowledged. ACK segments
are never acknowledged.
<small></small> <i>Retransmission: In modent implementations, a </i>
retransmissimt occur s if the retransmission timer
expires or three duplicate ACK segments have arrived.
</div><span class="text_page_counter">Trang 83</span><div class="page_container" data-page="83"><b>1.3 Mơ hình TCP/IP</b>
<small></small> <i><b>Out-of-Order Segments: Data may arrive out of order </b></i>
and be temporarily stored by the receiving TCP,
but TCP guarantees that no out-of-order segment is delivered to the process.
</div><span class="text_page_counter">Trang 84</span><div class="page_container" data-page="84"><b>1.3 Mơ hình TCP/IP</b>
<small></small> <b>Congestion Control: Congestion control refers to </b>
techniques and mechanisms that can either prevent congestion, before it happens, or remove congestion,
<b>after it has happened. Congestion control involves two </b>
factors that measure the performance of a network:
<i>delay and throughput</i>
</div><span class="text_page_counter">Trang 85</span><div class="page_container" data-page="85"><b>1.3 Mơ hình TCP/IP</b>
<i>Congestion Window:</i>
<i>Congestion Policy: TCP's general policy for handling </i>
congestion is based on three phases: slow start, congestion avoidance, and congestion detection. In the slow-start
phase, the sender starts with a very slow rate of
transmission, but increases the rate rapidly to reach a
threshold. When the threshold is reached, the data rate is reduced to avoid congestion. Finally if congestion is
detected, the sender goes back to the slow-start or
congestion avoidance phase based on how the congestion
</div><span class="text_page_counter">Trang 87</span><div class="page_container" data-page="87"><b>1.3 Mơ hình TCP/IP</b>
<b><small>d) </small></b>Application Layer:
<i>The application layer in TCP/IP is equivalent to the </i>
combined session, presentation, and application layers in the OSI model. Many protocols are defined at this layer.
</div><span class="text_page_counter">Trang 88</span><div class="page_container" data-page="88"><b>1.3 Mơ hình TCP/IP</b>
<b>Mapping Layer 3 to Layer 4</b>
</div><span class="text_page_counter">Trang 89</span><div class="page_container" data-page="89"><b>1.3 Mô hình TCP/IP</b>
<b>Mapping Layer 4 to Applications</b>
</div><span class="text_page_counter">Trang 91</span><div class="page_container" data-page="91"><b>1.3 Mơ hình TCP/IP</b>
<i><b>Relationship of layers and addresses in TCP/IP:</b></i>
</div><span class="text_page_counter">Trang 92</span><div class="page_container" data-page="92"><small>-</small> The physical addresses have authority over the
network (LAN or WAN). The size and format of these addresses vary depending on the network. For
example, Ethernet
uses a 6-byte (48-bit) physical address that is imprinted on the network interface card (NIC).
</div><span class="text_page_counter">Trang 93</span><div class="page_container" data-page="93"><b>1.3 Mơ hình TCP/IP</b>
<b><small>-Ví dụ: </small></b><i><b><small>a node with physical address 10 sends a frame to a node with physical address 87. The two nodes are connected by a link (bus topology LAN). As the figure shows, the computer with </small></b></i>
<i><b><small>physical address 10is the sender, and the computer with physical address 87is the receiver.</small></b></i>
</div><span class="text_page_counter">Trang 94</span><div class="page_container" data-page="94"><b>1.3 Mơ hình TCP/IP</b>
<small></small> <b>Logical Addresses: </b>
<small>-Logical addresses are necessary for universal communicationsthat are independent of underlying physical networks. Physicaladdresses are not adequate in an internetwork environmentwhere different networks can have different address formats. Auniversal addressing system is needed in which each host canbe identified uniquely, regardless of the underlying physicalnetwork.</small>
<small>- A logical address in the Internet is currently a 32-bit address that can uniquely define a host connected to the Internet. No two </small>
<small>publicly addressed and visible hosts on the Internet can have the </small>
<b><small>same lP address</small></b>.
</div>