Microsoft Press transitioning your mcsa mcse to windows server 2008 2009 phần 2 pot
Bạn đang xem bản rút gọn của tài liệu. Xem và tải ngay bản đầy đủ của tài liệu tại đây (2.17 MB, 97 trang )
Lesson 1: Confi guring Routing CHAPTER 2 69
Layer 2 and Layer 3 Addresses
T
he destination IP address (a Layer 3 address) of a packet never changes; it is
always set to the IP address of the target computer. To forward packets to a
router without changing the destination IP address, computers use the media access
control (MAC) address (a Layer 2 address). Therefore, as the packet is forwarded
between networks, the source and destination IP addresses never change. However,
the source and destination MAC addresses are rewritten for every network between
the client and server.
Confi guring Static Routing with Routing and Remote Access
After installing the Network Policy and Access Services server role, you can view the IP rout-
ing table by right-clicking Roles\Network Policy and AccessServices\Routing And Remote
Access\IPv4\Static Routes and then selecting Show IP Routing Table. Routing And Remote
Access displays the static routing table (which does not include any dynamic routes added
from RIP). You install the Network Policy and Access Services server role and view the IP route
table in the practice session later in this lesson.
Using Routing Information Protocol
Static route table confi guration is effi cient if your network contains only a few (typically fi ve
or fewer) routers and the network confi guration does not frequently change. For larger (but
not very large) networks, typically containing up to 15 routers, or for networks in which the
network topology is liable to change—for example, a dynamic corporate network used by a
small but rapidly expanding organization—the use of a routing protocol is indicated.
The Microsoft software-based routing solution is not appropriate for large, complex net-
works in which hardware routers or layer 3 switches might be used. Consequently, Windows
Server 2008 supports Routing Information Protocol (RIP), which is designed for exchanging
routing information within a small to medium-size network.
RIP is simple to confi gure and deploy. However, it cannot scale to large or very large
networks. The maximum hop count RIP routers can use is 15, and networks that are more
than 15 hops away are considered unreachable. As networks grow larger in size, the periodic
announcements that each RIP router generates can cause excessive traffi c.
Layer 2 and Layer 3 Addresses
T
he destination IP address (a Layer 3 address) of a packet never changes; it is
always set to the IP address of the target computer. To forward packets to a
router without changing the destination IP address, computers use the media access
control (MAC) address (a Layer 2 address). Therefore, as the packet is forwarded
between networks, the source and destination IP addresses never change. However,
the source and destination MAC addresses are rewritten for every network between
the client and server.
70 CHAPTER 2 Confi guring IP Services
Compared to more sophisticated routing protocols (for example, OSPF), RIP has a high
recovery time. When the network topology changes, it can take several minutes before the
RIP routers reconfi gure themselves to the new network topology. While the network recon-
fi gures itself, routing loops might form that result in lost or undeliverable data. However,
using RIP still results in less delay and lost traffi c than manually reconfi guring route tables on
15 routers.
Initially, the route table for each router includes only the networks that are physically con-
nected. A RIP router periodically sends announcements that contain its route table entries
to inform other local RIP routers about the networks it can reach. RIPv1 uses IP broadcast
packets for its announcements. RIPv2 uses either multicast or broadcast packets for its
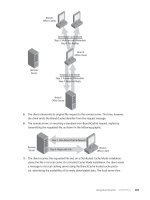
announcements. Figure 2-4 illustrates the route announcement process.
I can access
10.0.3.0/24 and 10.0.4.0/24,
so send packets for
those networks to me
I can access
10.0.1.0/24 and 10.0.2.0/24,
so send packets for
those networks to me
10.0.3.0/24
10.1.1.0/24
10.0.1.0/24
10.0.2.0/24
10.0.4.24
FIGURE 2-4 RIP announcements.
NOTE SILENT RIP
Silent RIP accepts updates from other systems but does not respond to requests or send
updates. By default, RIP sends a complete update to all neighbors and replies to all incom-
ing requests (LAN only). This is sometimes known as periodic RIP.
RIP routers can also communicate routing information through triggered updates. Trig-
gered updates occur when the network topology changes and updated routing information
is sent that refl ects those changes. RIP routers send triggered updates immediately and do
not wait for the next periodic announcement. Suppose, for example, that a RIP router detects
a link or router failure. It immediately updates its own route table and sends updated routes.
Each router that receives the triggered update modifi es its own route table and propagates
the change.
NOTE
SILENT RIP
NOTE SILENT RIPNOTE
Silent RIP accepts updates from other systems but does not respond to requests or send
updates. By default, RIP sends a complete update to all neighbors and replies to all incom-
ing requests (LAN only). This is sometimes known as periodic RIP.
Lesson 1: Confi guring Routing CHAPTER 2 71
Windows Server 2008 RRAS supports RIPv1 and RIPv2. RIPv2 supports multicast
announcements, simple password authentication, and more fl exibility in subnetted and
classless interdomain routing (CIDR) environments and is the default routing protocol for
Windows Server 2008.
The Windows Server 2008 implementation of RIP has the following features:
n
You can select which RIP version to run on each interface for incoming and outgoing
packets.
n
Split-horizon, poison-reverse, and triggered-update algorithms are used to avoid rout-
ing loops and to speed recovery of the network when topology changes occur.
n
You can use route fi lters to confi gure networks to ignore or accept announcements.
On the Security tab of the RIP Properties dialog box (discussed in Lesson 2), you can
confi gure the router to Accept Announcements From All Routers, Accept Announce-
ments From Listed Routers Only, or Ignore Announcements From Listed Routers.
n
You can use peer fi lters to choose which router’s announcements to accept.
n
Router announcements are confi gurable, and you can set route aging timers.
n
Simple password authentication is supported.
n
You can disable subnet summarization.
NOTE CONFIGURING ROUTING FROM THE COMMAND PROMPT
You can use the routing context of the netsh command to control announcements and
route advertisements from the command prompt. For example, the netsh routing ip rip
add peerfi lter server=10.10.10.161 command confi gures RIPv2 to accept announcements
from the router at 10.10.10.161. The announcefi lter option fi lters specifi c advertised routes
rather than accepting all updates from a particular router. You can use the netsh rout-
ing ipv6 add persistentroute command to add a static persistent IPv6 route to a particular
interface. You can use netsh routing ipv6 delete persistentroute to remove a persistent route
and netsh routing ipv6 show persistentroute to provide a list of all persistent routes. Netsh
routing ipv6 add fi lter adds an IPv6 packet fi lter to a specifi ed interface.
MORE INFO COUNT TO INFINITY
Even if a routing protocol supports split horizon with poison reverse, count-to-infi nity can
still occur in a multipath internetwork because routes to networks can be learned from
multiple sources. For more information about the count-to-infi nity problem, see http://
www.microsoft.com/technet/prodtechnol/windows2000serv/reskit/intwork/inae_ips_vzbs
.mspx?mfr=true. This is an old link, but the problem has not changed and is well described
here.
NOTE
CONFIGURING ROUTING FROM THE COMMAND PROMPT
NOTE CONFIGURING ROUTING FROM THE COMMAND PROMPTNOTE
You can use the routing context of the
netsh
command to control announcements and
route advertisements from the command prompt. For example, the
netsh routing ip rip
add peerfi lter server=10.10.10.161
command confi gures RIPv2 to accept announcements
from the router at 10.10.10.161. The
announcefi lter
option fi lters specifi c advertised routes
announcefi lter option fi lters specifi c advertised routes announcefi lter
rather than accepting all updates from a particular router. You can use the
netsh rout-
ing ipv6 add persistentroute
command to add a static persistent IPv6 route to a particular
interface. You can use
netsh routing ipv6 delete persistentroute
to remove a persistent route
and
netsh routing ipv6 show persistentroute
to provide a list of all persistent routes.
Netsh
routing ipv6 add fi lter
adds an IPv6 packet fi lter to a specifi ed interface.
routing ipv6 add fi lter adds an IPv6 packet fi lter to a specifi ed interface.routing ipv6 add fi lter
MORE INFO
COUNT TO INFINITY
Even if a routing protocol supports split horizon with poison reverse, count-to-infi nity can
still occur in a multipath internetwork because routes to networks can be learned from
multiple sources. For more information about the count-to-infi nity problem, see
http://
www.microsoft.com/technet/prodtechnol/windows2000serv/reskit/intwork/inae_ips_vzbs
.mspx?mfr=true
. This is an old link, but the problem has not changed and is well described
here.
72 CHAPTER 2 Confi guring IP Services
Split Horizon, Poison Reverse, and Triggered Updates
S
plit horizon helps reduce convergence time by not allowing routers to adver-
tise networks in the direction from which those networks are learned. The
information sent in RIP announcements is for those networks that are beyond the
neighboring router in the opposite direction. Networks learned from the neighbor-
ing router are not included.
Split horizon eliminates count-to-infi nity and routing loops during convergence in
single-path internetworks and reduces the chances of count-to-infi nity in multi-
path internetworks. Split horizon helps reduce convergence time because the only
information sent in RIP announcements is for those networks that are beyond the
neighboring router in the opposite direction.
Split horizon with poison reverse differs from simple split horizon because it
announces all networks. However, networks learned in the direction prohibited by
split horizon are announced with a hop count of 16, indicating that the network is
unreachable. In a single-path internetwork, split horizon with poison reverse has no
benefi t beyond split horizon. However, in a multipath internetwork, split horizon
with poison reverse reduces count-to-infi nity and routing loops.
Triggered updates enable a RIP router to announce changes in metric values almost
immediately rather than waiting for the next periodic announcement. A change to
a metric in an entry in the routing table triggers the update. For example, net-
works that become unavailable can be announced with a hop count of 16 through
a triggered update. This update is sent almost immediately. However, a small time
interval to wait is specifi ed on the router. If triggered updates were sent by all rout-
ers immediately, each triggered update could cause a cascade of broadcast traffi c
across the IPv4 network.
Triggered updates improve the convergence time of RIP internetworks but at the
expense of additional broadcast traffi c as the triggered updates are propagated.
Examining Network Routes
You can use the pathping and tracert commands to determine how packets travel between
your computer and a destination. Tracert provides a quicker response, but pathping provides
a more detailed analysis of network performance. Figure 2-5 and Figure 2-6 demonstrate how
pathping displays a route to the www.microsoft.com destination.
Split Horizon, Poison Reverse, and Triggered Updates
S
plit horizon helps reduce convergence time by not allowing routers to adver-
tise networks in the direction from which those networks are learned. The
information sent in RIP announcements is for those networks that are beyond the
neighboring router in the opposite direction. Networks learned from the neighbor-
ing router are not included.
Split horizon eliminates count-to-infi nity and routing loops during convergence in
single-path internetworks and reduces the chances of count-to-infi nity in multi-
path internetworks. Split horizon helps reduce convergence time because the only
information sent in RIP announcements is for those networks that are beyond the
neighboring router in the opposite direction.
Split horizon with poison reverse differs from simple split horizon because it
announces all networks. However, networks learned in the direction prohibited by
split horizon are announced with a hop count of 16, indicating that the network is
unreachable. In a single-path internetwork, split horizon with poison reverse has no
benefi t beyond split horizon. However, in a multipath internetwork, split horizon
with poison reverse reduces count-to-infi nity and routing loops.
Triggered updates enable a RIP router to announce changes in metric values almost
immediately rather than waiting for the next periodic announcement. A change to
a metric in an entry in the routing table triggers the update. For example, net-
works that become unavailable can be announced with a hop count of 16 through
a triggered update. This update is sent almost immediately. However, a small time
interval to wait is specifi ed on the router. If triggered updates were sent by all rout-
ers immediately, each triggered update could cause a cascade of broadcast traffi c
across the IPv4 network.
Triggered updates improve the convergence time of RIP internetworks but at the
expense of additional broadcast traffi c as the triggered updates are propagated.
Lesson 1: Configuring Routing CHAPTER 2 73
FIGURE 2-5 Route from source to destination.
FIGURE 2-6 Latency to each router.
Pathping shows the data in two sections. The first shows the route from the source to the
destination. The second shows the latency in milliseconds to each router.
The last line of the first section shows three asterisk (*) symbols. This occurs when a node
does not respond to the Internet Control Message Protocol (ICMP) requests. Sometimes serv-
ers are configured to ignore ICMP. Consequently, they will not appear in the list even though
they might be online and responding to other requests.
Figure 2-7 shows the output from the tracert www.microsoft.com command. The tracert
command completes quicker than pathping but gives less information.
74 CHAPTER 2 Configuring IP Services
FIGURE 2-7 Using tracert.
PracticE Installing and Configuring Routing
In this practice session, you install the Network Policy and Access Services server role and
Routing and Remote Access Services role service. You then configure your Windows Server
2008 server as a router.
ExErcisE 1 Install the Network Policy and Access Services Server Role
To install the Network Policy and Access Services server role, follow these steps:
1. Log on to your domain controller with the Kim_Akers account.
2. If Server Manager does not open automatically, click Start, and then select Server
Manager.
3. In the left pane, select Roles, and then, in the right pane, click Add Roles.
4. If the Before You Begin page appears, click Next.
5. On the Select Server Roles page, select the Network Policy and Access Services check
box, as shown in Figure 2-8, and then click Next.
Lesson 1: Configuring Routing CHAPTER 2 75
FIGURE 2-8 Adding the Network Policy and Access Services role.
6. On the Network Policy and Access Services page, click Next.
7. On the Role Services page, select the Routing and Remote Access Services check box.
The wizard automatically selects the Remote Access Service and Routing check boxes,
as shown in Figure 2-9.
8. Click Next.
FIGURE 2-9 Specifying the Routing and Remote Access Services role service.
76 CHAPTER 2 Configuring IP Services
9. On the Confirm Installation Selections page, click Install.
10. After the Add Roles Wizard completes the installation, click Close.
11. In the left-side pane of Server Manager, expand Roles, expand Network Policy and
Access Services, and then select Routing and Remote Access.
12. Right-click Routing and Remote Access, and then select Configure and Enable Routing
And Remote Access.
The Routing and Remote Access Server Setup Wizard appears.
13. On the Welcome To The Routing And Remote Access Server Setup Wizard page, click
Next.
14. On the Configuration page, select Custom Configuration, and then click Next.
15. On the Custom Configuration page, select the LAN Routing check box, as shown in
Figure 2-10, and then click Next.
FIGURE 2-10 Selecting the check box to configure LAN routing.
16. On the Completing The Routing And Remote Access Server Wizard page, click Finish.
17. Click Start Service. If you do not see this button, right-click Routing and Remote
Access, select All Tasks, and click Start.
ExErcisE 2 Use RRAS Graphical Tools to View and Configure Static Routes
In this exercise, you use the RRAS graphical tools in Server Manager to view the static route
table and to add and then remove a static route. You must perform Exercise 1 before you
attempt this exercise. To view, add, and delete static routes, follow these steps:
Lesson 1: Configuring Routing CHAPTER 2 77
1. In the Server Manager console tree, expand Roles, expand Network Policy and Access
Services, expand Routing and Remote Access, expand IPv4, right-click Static Routes,
and then select Show IP Routing Table.
The IPv4 route table is displayed as shown in Figure 2-11. The route table on your
domain controller will probably show different routes.
FIGURE 2-11 The IPv4 route table displayed through Server Manager.
2. Close the route table display. Right-click Static Routes, and then select New Static
Route.
3. In the IPv4 Static Route dialog box, select the network interface that will be used to
forward traffic to the remote network. In the Destination box, type the network ID of
the destination network. In the Network Mask box, type the subnet mask of the des-
tination network. In the Gateway box, type the router that packets for the destination
network should be forwarded to. Adjust metric only if you have multiple paths to the
same destination network and want to prefer one gateway over the others. In this case,
configure the preferred routes with lower metrics. The IPv4 Static Route dialog box
should look similar to Figure 2-12. Click OK.
FIGURE 2-12 Adding a static route.
78 CHAPTER 2 Configuring IP Services
Routing and Remote Access adds the static route, which is displayed in the Static
Routes pane.
4. Right-click the static route you have created, and then select Delete.
ExErcisE 3 Enable RIP
In this exercise, you enable RIP. This allows Windows Server 2008 to advertise routes to neigh-
boring routers and to detect neighboring routers and remote networks automatically. You
must perform Exercise 1 before you attempt this exercise. To enable RIP, follow these steps:
1. In the Server Manager console tree, expand Roles, expand Network Policy and Access
Services, expand Routing and Remote Access, expand IPv4, right-click General, and
then select New Routing Protocol.
2. In the New Routing Protocol dialog box, select RIP Version 2 For Internet Protocol, and
then click OK.
RIP appears under IPv4 in the left-side pane.
3. Right-click RIP, and then select New Interface.
4. In the New Interface for RIP Version 2 For Internet Protocol dialog box, select the inter-
face you want to advertise with RIP, as shown in Figure 2-13.
The interfaces on your domain controller might differ from those in the figure.
5. Click OK.
FIGURE 2-13 Selecting the interface you want to advertise with RIP.
6. Configure the RIP settings by using the RIP Properties dialog box.
In practice, on a production network, you would choose settings that match those
of neighboring routers. The default settings work in most environments. You can adjust
settings by using the four tabs of the dialog box. On the General tab, you can choose
Lesson 1: Confi guring Routing CHAPTER 2 79
whether RIPv1 or RIPv2 is used and whether authentication is required. On the Secu-
rity tab, you can choose whether to fi lter router advertisements. The Neighbors tab
enables you to list manually the neighbors with which the computer communicates.
The Advanced tab confi gures announcement intervals, which defi ne how frequently a
router announces its routes, time-outs, and other infrequently used settings.
7. Click OK when you have completed the confi guration. Repeat this process for every
interface that has routing enabled.
NOTE FILTERING ROUTER ADVERTISEMENTS
Because RIP can be used to advertise a route to a malicious computer, it can be used as
part of a man-in-the-middle attack. Therefore, restrict the advertised routes that are
accepted whenever possible.
Lesson Summary
n
You can confi gure software-based routing on a Windows Server 2008 server to allow
software-based routers to forward traffi c between each other and enable clients and
servers on different subnets to communicate.
n
You can use static routing to allow computers with multiple routers connected to their
subnet to forward traffi c with different destinations to the correct subnet.
n
You can use pathping and tracert to identify the routers between a source and a desti-
nation. You can use both tools to identify routing problems.
n
Windows Server 2008 supports RIP, which you can enable by installing the Routing and
Remote Access Services role service.
Lesson Review
You can use the following questions to test your knowledge of the information in Lesson 1,
“Confi guring Routing.” The questions are also available on the companion DVD if you prefer
to review them in electronic form.
NOTE LESSON REVIEW ANSWERS
Answers to these questions and explanations of why each answer choice is right or wrong
are located in the “Answers” section at the end of the book.
1. Currently, client computers on the 10.0.0.0/24 subnet are confi gured with the 10.0.0.11
default gateway. You connect a second router to both the 10.0.0.0/24 subnet and the
10.0.1.0/24 subnet. You would like clients on the 10.0.0.0/24 subnet to connect to
the 10.0.1.0/24 subnet by using the new router, which has the 10.0.0.21 IP address on
the 10.0.0.0/24 subnet. Which command should you run?
NOTE
FILTERING ROUTER ADVERTISEMENTS
NOTE FILTERING ROUTER ADVERTISEMENTSNOTE
Because RIP can be used to advertise a route to a malicious computer, it can be used as
part of a man-in-the-middle attack. Therefore, restrict the advertised routes that are
accepted whenever possible.
NOTE
LESSON REVIEW ANSWERS
NOTE LESSON REVIEW ANSWERSNOTE
Answers to these questions and explanations of why each answer choice is right or wrong
are located in the “Answers” section at the end of the book.
80 CHAPTER 2 Configuring IP Services
A. route add 10.0.1.0 MASK 255.255.255.0 10.0.0.11
B. route add 10.0.1.0 MASK 255.255.255.0 10.0.0.21
C. route add 10.0.0.0 MASK 255.255.255.0 10.0.0.21
D. route add 10.0.0.21 MASK 255.255.255.0 10.0.1.0
2. Which of the following are supported by Windows Server 2003 but not by Windows
Server 2008? (Choose all that apply.)
A. RIPv2
B. NWLink
C. Services for Macintosh
D. Basic Firewall
E. OSPF
F. SSTP
3. You configure a computer running Windows Server 2008 with two network interfaces.
Each interface is connected to a different subnet. One of those subnets has four other
routers connected to it, and each router provides access to several subnets. You would
like the computer running Windows Server 2008 to automatically identify the routers
and determine which remote subnets are available using each router. What should
you do?
A. Enable NAT on the interface.
B. Enable RIP on the interface.
C. Enable OSPF on the interface.
D. Add a static route to the interface.
4. You use the route print command on a Windows Server 2008 server and examine the
IPv6 route table. Which of the following are host routes for a specific IPv6 destination?
(Choose all that apply.)
A. fe80::4c81:2382:92ad:130f/128
B. fe80::8860:8bf:9cb8:80eb/128
C. fe80::/64
D. ff00::/8
5. You are experiencing intermittent connectivity problems accessing an internal Web site
on a remote network. You would like to view a list of routers between the client and
the server. Which tools can you use? (Choose all that apply.)
A. ping
B. ipconfig
C. pathping
D. tracert
Lesson 2: Confi guring IPsec CHAPTER 2 81
Lesson 2: Confi guring IPsec
By enforcing trusted communication, you can use IPsec to secure communication between
two hosts or to secure traffi c across external networks, including the Internet in VPN scenar-
ios. IPsec is invisible to the end user and secures communication over the entire path between
the source and the destination. You can manage IPsec through Local Security Policy, Group
Policy, or command-line tools. This lesson discusses how you deploy IPsec and concentrates
mainly on deployment through Group Policy.
After this lesson, you will be able to:
n
Describe the various methods by which you can deploy IPsec.
n
Deploy IPsec on a network through Group Policy.
n
Distinguish between encryption and authentication and know which protocols
and methods can be used to secure network communication.
n
Understand netsh contexts and use netsh commands, particularly commands in
the netsh advfi rewall consec context, to manage IPsec rules.
Estimated lesson time: 60 minutes
REAL WORLD
Ian McLean
I
fi rst came across IPsec in 1999, and it implemented some important security fea-
tures. First, it could secure communication between a source and destination that
could support it, even if intermediate stations did not. IPsec could secure all com-
munications, whereas protocols such as Secure Sockets Layer (SSL) could secure only
Web traffi c. Most signifi cant, IPsec was invisible to the user, and what users don’t
know about they don’t complain about.
Those of us who had to confi gure and administer IPsec tended to be less keen on it.
It was not easily understood or confi gured, you needed to understand soft and hard
associations, and the debugging tools we used every day, for example, ping didn’t
work anymore (at least not until the association was established).
After this lesson, you will be able to:
n
Describe the various methods by which you can deploy IPsec.
n
Deploy IPsec on a network through Group Policy.
n
Distinguish between encryption and authentication and know which protocols
and methods can be used to secure network communication.
n
Understand
netsh
contexts and use
netsh
commands, particularly commands in
the
netsh advfi rewall consec
context, to manage IPsec rules.
netsh advfi rewall consec context, to manage IPsec rules.netsh advfi rewall consec
Estimated lesson time: 60 minutes
REAL WORLD
Ian McLean
I
fi rst came across IPsec in 1999, and it implemented some important security fea-
tures. First, it could secure communication between a source and destination that
could support it, even if intermediate stations did not. IPsec could secure all com-
munications, whereas protocols such as Secure Sockets Layer (SSL) could secure only
Web traffi c. Most signifi cant, IPsec was invisible to the user, and what users don’t
know about they don’t complain about.
Those of us who had to confi gure and administer IPsec tended to be less keen on it.
It was not easily understood or confi gured, you needed to understand soft and hard
associations, and the debugging tools we used every day, for example,
ping
didn’t
work anymore (at least not until the association was established).
82 CHAPTER 2 Confi guring IP Services
Windows Server 2008 introduces new methods of confi guring IPsec through con-
nection security rules. If you need to confi gure standard IPsec policies and do not
require encryption, this greatly simplifi es confi guration. If you need to refi ne your
confi guration, you can do this through Windows Firewall with Advanced Secu-
rity (WFAS) or netsh advfi rewall commands. IPsec policies are retained and will
undoubtedly still be used by those familiar with IPsec confi guration in previous
Windows operating systems, but now you have the choice.
L2TP/IPsec is now the standard way of encrypting and authenticating a VPN tun-
nel. Windows Server 2008 does not change IPsec fundamentally, but it introduces
some important enhancements, discussed in this lesson. Love it or hate it, IPsec is
here to stay, and IPsec confi guration will almost certainly be tested in your upgrade
examinations.
Implementing IPsec
As an experienced administrator, you know that IPsec provides a method of protecting data
on an IP network by ensuring authenticity, confi dentiality, or both. However, if you do not
confi gure IPsec on a regular basis, you might need some review before you go on to look at
the new features Windows Server 2008 introduces.
The Windows implementation of IPsec is based on standards developed by the Internet
Engineering Task Force (IETF) IPsec working group. IPsec provides security for data sent
between two computers on an IP network. It protects data between two IP addresses by
providing the following services:
n
Data Authentication IPsec provides data origin authentication. You can confi gure it
to ensure that each packet you receive from a trusted party genuinely originates from
that party and is not spoofed. The protocol also ensures data integrity and can ensure
that data is not altered in transit. You can implement anti-replay protection by confi g-
uring IPsec to verify that each packet received is unique and not duplicated.
n
Encryption You can use IPsec to encrypt network data so that the data is unreadable
if captured in transit.
In Windows Server 2008, you confi gure IPsec through either IPsec policies or connection
security rules. By default, IPsec policies attempt to negotiate both authentication and encryp-
tion services. Connection security rules, by default, attempt to negotiate only authentication
services. You can, however, confi gure IPsec policies and connection security rules to provide
any combination of data protection services.
Windows Server 2008 introduces new methods of confi guring IPsec through con-
nection security rules. If you need to confi gure standard IPsec policies and do not
require encryption, this greatly simplifi es confi guration. If you need to refi ne your
confi guration, you can do this through Windows Firewall with Advanced Secu-
rity (WFAS) or
netsh advfi rewall
commands. IPsec policies are retained and will
netsh advfi rewall commands. IPsec policies are retained and will netsh advfi rewall
undoubtedly still be used by those familiar with IPsec confi guration in previous
Windows operating systems, but now you have the choice.
L2TP/IPsec is now the standard way of encrypting and authenticating a VPN tun-
nel. Windows Server 2008 does not change IPsec fundamentally, but it introduces
some important enhancements, discussed in this lesson. Love it or hate it, IPsec is
here to stay, and IPsec confi guration will almost certainly be tested in your upgrade
examinations.
Lesson 2: Confi guring IPsec CHAPTER 2 83
NOTE IPSEC BEYOND WINDOWS
Because it is an interoperable standard, you can implement IPsec to secure communica-
tions between computers running Windows and those that don’t.
In Windows Server 2008 networks, you typically implement IPsec through Group Policy,
either by using IPsec policies or through connection security rules. The connection security
rules method is new to Windows Server 2008 and is typically used in combination with WFAS.
As a Windows Server 2003 administrator, you will be more familiar with the concepts behind
IPsec policies.
Using Connection Security Rules
Windows Server 2008 refers to IPsec rules as connection security rules. They perform the
same function as the IPsec rules available in previous versions of Windows but support more
advanced authentication and encryption algorithms.
In previous versions of Windows, implementations of server or domain isolation sometimes
required the creation of a large number of IPsec rules to make sure that required network
traffi c was protected while still permitting required network traffi c that could not be secured
with IPsec. Windows Server 2008 eases this complexity by a new default behavior that results
in a more secure environment that is easier to troubleshoot.
MORE INFO DOMAIN ISOLATION
For more information about domain isolation in Windows Server 2008, see http://technet
.microsoft.com/en-us/library/cc770610.aspx.
Windows Server 2008 introduces connection security rules, which facilitate implement-
ing IPsec for authenticated communication on a network. Windows Server 2008 gives you
the option of enforcing connection security rules through a Group Policy object (GPO) in the
WFAS node.
Connection security rules evaluate network traffi c and then block, allow, or negotiate
security for messages based on the criteria you confi gure. Unlike IPsec policies, connection
security rules do not include fi lters or fi lter actions. The features provided by fi lters and fi lter
actions are built into each connection security rule, but the fi ltering capabilities in connection
security rules are not as powerful as those of IPsec policies. If further, more complex fi lter-
ing is required, you can use WFAS or netsh to implement this. By default, connection security
rules do not apply to types of IP traffi c such as IP traffi c that passes over port 23. Instead, they
apply to all IP traffi c originating from or destined for certain IP addresses, subnets, or servers
on the network.
NOTE
IPSEC BEYOND WINDOWS
NOTE IPSEC BEYOND WINDOWSNOTE
Because it is an interoperable standard, you can implement IPsec to secure communica-
tions between computers running Windows and those that don’t.
MORE INFO
DOMAIN ISOLATION
For more information about domain isolation in Windows Server 2008, see
http://technet
.microsoft.com/en-us/library/cc770610.aspx
.
.microsoft.com/en-us/library/cc770610.aspx microsoft.com/en-us/library/cc770610.aspx
84 CHAPTER 2 Confi guring IP Services
A connection security rule fi rst authenticates the computers defi ned in the rule before they
begin communicating and then secures the information sent between these two authenti-
cated computers. If you have confi gured a connection security rule that requires security for
a given connection, and the two computers in question cannot authenticate each other, the
connection is blocked.
By default, connection security rules provide only data authentication security (data
origin authentication, data integrity, and anti-replay security). For this reason, connection
security rules typically authenticate only connections. You can, however, also confi gure data
encryption for connection security rules (typically through WFAS) so that the connections in
question are truly secured and not merely authenticated.
REAL WORLD
Ian McLean
T
he advantage of connection security rules lies in their simplicity. Most admin-
istrators choose to use connection security rules to perform only their default
functions and implement more complex functions, such as port or IP fi ltering,
through WFAS. You can also use IPsec policies when you require (for example)
data encryption, and those familiar with IPsec confi guration in Windows Server
2003 might be more comfortable with this method. It is diffi cult to say for certain
whether the new methods of IPsec confi guration will be more comprehensively
tested in the upgrade examinations than will be the more familiar methods,
although in my experience, examiners often concentrate on new features. My
advice: know both methods.
Connection security rules are confi gured in the WFAS console. You can enforce specifi c
WFAS console settings on a network by using Group Policy. Figure 2-14 shows a GPO that
defi nes connection security rules for many computers on a network.
REAL WORLD
Ian McLean
T
he advantage of connection security rules lies in their simplicity. Most admin-
istrators choose to use connection security rules to perform only their default
functions and implement more complex functions, such as port or IP fi ltering,
through WFAS. You can also use IPsec policies when you require (for example)
data encryption, and those familiar with IPsec confi guration in Windows Server
2003 might be more comfortable with this method. It is diffi cult to say for certain
whether the new methods of IPsec confi guration will be more comprehensively
tested in the upgrade examinations than will be the more familiar methods,
although in my experience, examiners often concentrate on new features. My
advice: know both methods.
Lesson 2: Confi guring IPsec CHAPTER 2 85
FIGURE 2-14 Connection security rules can be defined in Group Policy.
NOTE EXPORTING CONNECTION SECURITY RULES
You can use the Export Policy and Import Policy functions in the WFAS console to create a
set of connection security rules and export them to other computers or GPOs.
Using Windows Firewall with Advanced Security
In Windows Server 2008, you can use a single tool, the WFAS MMC snap-in, to confi gure both
Windows Firewall and IPsec. The new WFAS builds on the default confi guration implemented
by the connection security rules described in the previous section. By combining IPsec con-
nection security rules and fi rewall fi lters into a single policy, Windows Firewall implements
policy-driven network access, resulting in more intelligent authenticating fi rewall actions.
MORE INFO POLICY-DRIVEN NETWORK ACCESS
Do not confuse policy-driven network access with IPsec confi guration through IPsec
policies. For more information about policy-driven network access, see
/>WFAS is on by default and consolidates and enhances the two functions, which were
managed separately in previous versions of Windows Server. In addition to the new graphical
user interface (GUI) tool, you can also manage both Windows Firewall and IPsec from the
command-line netsh advfi rewall context as discussed in the next section of this lesson.
NOTE
EXPORTING CONNECTION SECURITY RULES
NOTE EXPORTING CONNECTION SECURITY RULESNOTE
You can use the Export Policy and Import Policy functions in the WFAS console to create a
set of connection security rules and export them to other computers or GPOs.
MORE INFO
POLICY-DRIVEN NETWORK ACCESS
Do not confuse policy-driven network access with IPsec confi guration through IPsec
policies. For more information about policy-driven network access, see
/>.
/> 86 CHAPTER 2 Configuring IP Services
By default, all IPv4 and IPv6 incoming traffic is blocked unless it is a response to a previous
outgoing request from the computer (solicited traffic) or specifically allowed by a rule created
to allow that traffic. All outgoing traffic is allowed by default, except where service-hardening
rules prevent standard services from communicating in unexpected ways. You can allow
traffic based on port numbers, IPv4 or IPv6 addresses, the path and name of an application,
the name of a service that is running on the computer, or other criteria.
You can protect network traffic entering or exiting the computer by using the IPsec
protocol to verify the integrity of the network traffic, to authenticate the identity of the
sending and receiving computers or users, and, optionally, to encrypt traffic to provide
confidentiality. You set up a rule by creating a WFAS inbound rule—for example, a rule that
identifies an incoming port such as 443, specifying that the connection is allowed only if it
is secure, and requiring encryption. You can then finish the rule creation and edit the WFAS
rule you have created to specify to which IP addresses it applies. This method enables you to
specify the source and destination IP address as well as the ports that require IPsec encryp-
tion and specific authentication methods. Figure 2-15 shows the dialog boxes you would use
to create a rule by this method. These include the Custom Data Protection Settings dialog box
together with the WFAS GUI and the Customize IPsec Settings dialog box.
FIGURE 2-15 IPsec rule configuration dialog boxes.
Lesson 2: Confi guring IPsec CHAPTER 2 87
MORE INFO CONFIGURING IPSEC TO USE NETWORK ACCESS POLICY (NAP) RULES
Using connection security rules and refi ning IPsec policy through WFAS enables you to
specify a NAP rule together with or instead of an IPsec rule as part of IPsec policy. For more
information, see
For more information about NAP, see Chapter 4, “Confi guring Network Access Security.”
Netsh Commands for IPsec
As with almost all administrative functions, you can use the network shell command (netsh)
instead of graphical tools to administer IPsec. However, the netsh ipsec context, which you
might have used to administer Windows Server 2003 IPsec, is not the best tool for Windows
Server 2008. The netsh ipsec static and netsh ipsec dynamic contexts are still provided, but
they are for compatibility with previous versions of Windows. They do not enable you to
manage or interact with any of the IPsec features that are new to Windows Server 2008.
Microsoft recommends that you use the netsh advfi rewall context instead.
MORE INFO NETSH IPSEC
If you want to remind yourself about how the tools provided in the netsh ipsec static
and netsh ipsec dynamic contexts work, see />/cc725926.aspx.
MORE INFO HOW TO USE NETSH ADVFIREWALL
For more information about the netsh advfi rewall commands that replace the netsh ipsec
commands in Windows Server 2008, see For
examination purposes, investigate netsh advfi rewall and ascertain how you would verify
that IPsec is enabled.
Administering IPsec from the command line is especially useful when you want to accom-
plish the following:
n
Script IPsec confi guration
n
Extend the security and manageability of IPsec by confi guring the following features,
which are not available in the IP Security Policy Management snap-in:
•
IPsec diagnostics
•
Default traffi c exemptions
•
Strong certifi cate revocation list (CRL) checking
•
IKE (Oakley) logging
MORE INFO
CONFIGURING IPSEC TO USE NETWORK ACCESS POLICY (NAP) RULES
Using connection security rules and refi ning IPsec policy through WFAS enables you to
specify a NAP rule together with or instead of an IPsec rule as part of IPsec policy. For more
information, see
/>.
/>For more information about NAP, see Chapter 4, “Confi guring Network Access Security.”
MORE INFO
NETSH IPSEC
If you want to remind yourself about how the tools provided in the
netsh ipsec static
and
netsh ipsec dynamic
contexts work, see
netsh ipsec dynamic contexts work, see netsh ipsec dynamic
/>/cc725926.aspx
.
/cc725926.aspx./cc725926.aspx
MORE INFO
HOW TO USE
NETSH ADVFIREWALL
For more information about the
netsh advfi rewall
commands that replace the
netsh ipsec
commands in Windows Server 2008, see
/>. For
examination purposes, investigate
netsh advfi rewall
and ascertain how you would verify
netsh advfi rewall and ascertain how you would verify netsh advfi rewall
that IPsec is enabled.
88 CHAPTER 2 Confi guring IP Services
•
Logging intervals
•
Computer startup security
•
Computer startup traffi c exemptions
NOTE RUN AS ADMINISTRATOR
If you are using netsh to confi gure IPsec (and for most other netsh confi gurations), you
must run the Command Prompt console as an administrator.
Netsh advfi rewall is a command-line context for WFAS by which you create, administer,
and monitor Windows Firewall and IPsec settings. The tool is especially useful in the following
situations:
n
You are deploying WFAS settings to computers on a wide area network (WAN). You
can use the commands interactively at the netsh command prompt to provide better
performance than graphical utilities across slow-speed network links.
n
When deploying WFAS settings to a large number of computers, you can use netsh
advfi rewall commands in batch mode at the netsh command prompt to help script and
automate administrative tasks.
NOTE NETSH FIREWALL
The netsh fi rewall context is supplied for backward compatibility. Microsoft recommends
that you do not use this context on a computer that is running Windows Server 2008.
The available contexts for managing Windows Firewall with Advanced Security are as
follows:
n
Netsh advfi rewall
n
Netsh advfi rewall consec
n
Netsh advfi rewall fi rewall
n
Netsh advfi rewall monitor
The Netsh Advfi rewall Context
Netsh advfi rewall can be regarded as a separate context from the other three previously
listed, although the other contexts are actually subcontexts of netsh advfi rewall. This con-
text provides commands that are common to all WFAS settings, including IPsec settings. For
example, you might want to export a WFAS confi guration that includes IPsec settings from
one computer and import the confi guration into other computers. The following commands
are available at the netsh advfi rewall> prompt:
n
dump
n
export
NOTE
RUN AS ADMINISTRATOR
NOTE RUN AS ADMINISTRATORNOTE
If you are using
netsh
to confi gure IPsec (and for most other
netsh
confi gurations), you
must run the Command Prompt console as an administrator.
NOTE
NETSH
FIREWALL
NETSH FIREWALLNETSH
The
netsh
fi rewall context is supplied for backward compatibility. Microsoft recommends
that you do not use this context on a computer that is running Windows Server 2008.
Lesson 2: Confi guring IPsec CHAPTER 2 89
n
import
n
reset
n
set
n
show
Dump The dump command is available but not implemented for the netsh advfi rewall con-
text or any of its three subcontexts. It produces no output but also generates no error.
Export The export command exports the WFAS confi guration in the current store to a fi le.
This fi le can be used with the import command to restore the WFAS service confi guration to a
store on the same computer or to a different computer. The WFAS confi guration on which the
export command works is determined by the set store command. This command is equivalent
to the Export Policy command in the WFAS Microsoft Management Console (MMC) snap-in.
Import The import command imports a WFAS service confi guration from a fi le created by
using the export command to the local service. The command is equivalent to the Import
Policy command in the WFAS MMC snap-in.
Reset The reset command restores WFAS to its default settings and rules. Optionally, it fi rst
backs up the current settings by using the export command to export them to a confi guration
fi le. The command is equivalent to the Restore Defaults command in the WFAS MMC snap-in.
If the current focus of your commands is the local computer object, the default settings
and rules immediately take effect on the computer. If the current focus of your commands is a
GPO, the reset command resets all policy settings in that object to Not Confi gured and deletes
all connection security and fi rewall rules from the object. Changes do not take place until that
policy is refreshed on those computers to which the policy applies. To modify a GPO rather
than the local computer’s confi guration store, you would use the set store command.
Set The netsh advfi rewall context provides three set commands that confi gure settings that
apply either globally or to the per-profi le confi gurations of WFAS. The set commands avail-
able at the netsh advfi rewall prompt are:
n
set {Pro leType}
n
set global
n
set store
NOTE DEFAULT PROFILE STATE
The default state for all profi les on computers that are running a new installation of
Windows Server 2008 is on. For computers that were upgraded to Windows Server 2008
from an earlier version of Windows Server, the state of WFAS is preserved from the state
of Windows Firewall on the previously installed operating system.
NOTE
DEFAULT PROFILE STATE
NOTE DEFAULT PROFILE STATENOTE
The default state for all profi les on computers that are running a new installation of
Windows Server 2008 is
on
. For computers that were upgraded to Windows Server 2008
from an earlier version of Windows Server, the state of WFAS is preserved from the state
of Windows Firewall on the previously installed operating system.
90 CHAPTER 2 Confi guring IP Services
Show The show command displays settings that apply either globally or to the per-profi le
confi gurations of WFAS. The following show commands are available at the netsh advfi rewall>
prompt:
n
show {Pro leType}
n
show global
n
show store
The Netsh AdvFirewall Consec Context
The netsh advfi rewall consec context enables you to view, create, and modify connection
security rules specifi cally related to IPsec. This context is the command-line equivalent of
the Connection Security Rules node of the WFAS MMC snap-in. The following commands are
available in this context:
n
add
n
set
n
show
n
delete
Add In the netsh advfi rewall consec context, the add command is used as the add rule
command to add a connection security rule that defi nes IPsec requirements for network con-
nections. For example, the following command creates a rule that you could use in a domain
isolation scenario in which incoming traffi c is permitted from other domain member comput-
ers only:
netsh advfirewall consec add rule name="Only Domain Members" endpoint1=any endpoint2=any
action=requireinrequestout
CAUTION DO NOT USE ALL AS A NAME
Do not create a connection security rule with the name all. This creates a confl ict with
the netsh option.
Set In the netsh advfi rewall consec context, the set command is used as the set rule com-
mand to modify an existing connection security rule identifi ed by name or found by matching
the criteria specifi ed. Criteria that precede the keyword new identify the rule(s) to be modi-
fi ed. Criteria that follow the keyword new indicate properties that are modifi ed or added. For
example, the following command modifi es the action in the Only Domain Members rule so
that the criteria for incoming traffi c are requested rather than required.
set rule name="Only Domain Members" new action=requestinrequestout
CAUTION
DO NOT USE ALL AS A NAME
CAUTION DO NOT USE ALL AS A NAMECAUTION
Do not create a connection security rule with the name
all
. This creates a confl ict with
the
netsh
option.
Lesson 2: Confi guring IPsec CHAPTER 2 91
Show In the netsh advfi rewall consec context, the show command is used as the show rule
command. For example, the following command displays all existing connection security
rules:
netsh advfirewall consec show rule name=all
Delete In the netsh advfi rewall consec context, the delete command is used as the delete
rule command to delete a connection security rule or a number of rules, all of which match
the criteria specifi ed in the command. For example, the following command deletes the Only
Domain Members rule that you created earlier:
netsh advfirewall consec delete rule name="Only Domain Members"
Other Netsh Advfi rewall Contexts
The netsh advfi rewall fi rewall and netsh advfi rewall monitor contexts are not relevant to IPsec
confi guration.
MORE INFO NETSH COMMANDS FOR WFAS
For more information about netsh commands for WFAS, including syntax information and
examples, see For
more information about WFAS, see Chapter 4, “Network Access Security.”
Using IPsec Policies
You can use IPsec policies to defi ne how a computer or group of computers handle IPsec
communication. You assign an IPsec policy to an individual computer by using Local Security
Policy or to a group of computers by using Group Policy. You can specify several IPsec policies
for use on a computer or network, but only one policy is assigned to a computer at any given
time. Figure 2-16 shows a GPO in which an IPsec policy is assigned.
An IPsec policy contains one or more IPsec policy
rules. These rules determine when and
how IP traffi c is protected. Each policy rule, in turn, is associated with one IP fi lter list and one
fi lter action.
MORE INFO
NETSH
COMMANDS FOR WFAS
NETSH COMMANDS FOR WFASNETSH
For more information about
netsh
commands for WFAS, including syntax information and
examples, see
/>. For
more information about WFAS, see Chapter 4, “Network Access Security.”
92 CHAPTER 2 Confi guring IP Services
FIGURE 2-16 IPsec policies assigned in a GPO.
An IP fi lter list contains one or more IP fi lters that defi ne the IP traffi c affected by an IPsec
policy. An IP fi lter can defi ne a source or destination address, an address range, a computer
name, a TCP/UDP port, or a server type (DNS, WINS, DHCP, or default gateway). If traffi c
leaving or arriving at a computer on which a policy is assigned matches a fi lter in one of the
assigned policy’s policy rules, the fi lter action associated with that rule is applied. Possible
fi lter actions for a rule include
block, permit, or negotiate security. When matching a source
or destination address, the most specifi c IPsec fi lter always takes precedence.
Security Negotiation
N
egotiate Security is a general fi lter action option. If you specify this option, you
can then specifi cally choose the way security is negotiated for the fi lter action.
For example, should encryption be negotiated or merely authentication? What is
the order of preference for encryption technologies or hashing algorithms? Is it
permissable to use unsecured communications if the source and destination cannot
agree on a common protocol for security?
You can choose many ways to negotiate security for a fi lter action, and it is there-
fore possible to defi ne many distinct rules when you select the Negotiate Security
option. Security can be successfully negotiated only when both ends of an IPsec
connection can agree on the particular services and algorithms used to protect the
data.
Security Negotiation
N
egotiate Security
is a general fi lter action option. If you specify this option, you
egotiate Security is a general fi lter action option. If you specify this option, you egotiate Security
can then specifi cally choose the way security is negotiated for the fi lter action.
For example, should encryption be negotiated or merely authentication? What is
the order of preference for encryption technologies or hashing algorithms? Is it
permissable to use unsecured communications if the source and destination cannot
agree on a common protocol for security?
You can choose many ways to negotiate security for a fi lter action, and it is there-
fore possible to defi ne many distinct rules when you select the Negotiate Security
option. Security can be successfully negotiated only when both ends of an IPsec
connection can agree on the particular services and algorithms used to protect the
data.
Lesson 2: Confi guring IPsec CHAPTER 2 93
Figure 2-17 illustrates an IPsec policy and how that policy is composed of rules, fi lters, and
fi lter actions. In the fi gure, the IPsec policy consists of three rules. The fi rst rule has priority
because it defi nes traffi c most specifi cally—both by type (Telnet or IMAP4) and by address
(from 10.0.0.11 or from 10.0.0.31). The second rule is the next most specifi c, defi ning traffi c
by type (Telnet or IMAP4). The third rule is the least specifi c because it applies to all traffi c. It,
therefore, has the lowest priority.
A computer to which the IPsec policy illustrated in Figure 2-17 is assigned will attempt to
authenticate (but not encrypt) all data except Telnet and IMAP4 traffi c. Telnet and IMAP4
traffi c are blocked by default unless the Telnet traffi c originates from 10.0.0.11 or the IMAP4
traffi c originates from 10.0.0.31, in which case, the traffi c is allowed if encryption can be suc-
cessfully negotiated.
IPsec Policy
Less specific/Lower priority
IP Filter Lists Filter Actions
Policy Rule #1
Policy Rule #2
Policy Rule #3
Filter #1: Telnet Traffic from 10.0.0.11
Filter #2: IMAP4 Traffic from 10.0.0.31
Filter #1: All Telnet Traffic
Filter #2: All IMAP4 Traffic
Negotiate Security
(Require Encryption)
Negotiate Security
(Request Authentication)
Filter #1: All Traffic
Block
FIGURE 2-17 An IPsec policy that consists of three rules.
Quick Check
1. What are the possible fi lter actions for an IPsec rule?
2. What does a fi lter action within an IPsec policy do?
Quick Check Answers
1. Block, permit, negotiate security.
2. A fi lter action determines whether the traffi c captured by an IP fi lter in a given
policy rule is permitted, blocked, encrypted, or authenticated.
Quick Check
1
. What are the possible fi lter actions for an IPsec rule?
2
. What does a fi lter action within an IPsec policy do?
Quick Check Answers
1
. Block, permit, negotiate security.
2
. A fi lter action determines whether the traffi c captured by an IP fi lter in a given
policy rule is permitted, blocked, encrypted, or authenticated.
1
2
1
2
Quick Check
1