Tài liệu How To Do Everything With Windows XP Home Networking- P1 doc
Bạn đang xem bản rút gọn của tài liệu. Xem và tải ngay bản đầy đủ của tài liệu tại đây (1.04 MB, 50 trang )
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
Windows
®
XP
Home
Networking
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
This page intentionally left blank
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
Windows
®
XP
Home
Networking
Dave Field
Andrew Brandt
McGraw-Hill/Osborne
New York Chicago San Francisco Lisbon
London Madrid Mexico City Milan New Delhi
San Juan Seoul Singapore Sydney Toronto
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
Copyright © 2004 by McGraw-Hill Companies. All rights reserved. Manufactured in the United States of America. Except as permit-
ted under the United States Copyright Act of 1976, no part of this publication may be reproduced or distributed in any form or by any
means, or stored in a database or retrieval system, without the prior written permission of the publisher.
0-07-226434-9
The material in this eBook also appears in the print version of this title: 0-07-225809-8.
All trademarks are trademarks of their respective owners. Rather than put a trademark symbol after every occurrence of a trademarked
name, we use names in an editorial fashion only, and to the benefit of the trademark owner, with no intention of infringement of the
trademark. Where such designations appear in this book, they have been printed with initial caps.
McGraw-Hill eBooks are available at special quantity discounts to use as premiums and sales promotions, or for use in corporate train-
ing programs. For more information, please contact George Hoare, Special Sales, at or (212) 904-
4069.
TERMS OF USE
This is a copyrighted work and The McGraw-Hill Companies, Inc. (“McGraw-Hill”) and its licensors reserve all rights in and to the
work. Use of this work is subject to these terms. Except as permitted under the Copyright Act of 1976 and the right to store and retrieve
one copy of the work, you may not decompile, disassemble, reverse engineer, reproduce, modify, create derivative works based upon,
transmit, distribute, disseminate, sell, publish or sublicense the work or any part of it without McGraw-Hill’s prior consent. You may
use the work for your own noncommercial and personal use; any other use of the work is strictly prohibited. Your right to use the work
may be terminated if you fail to comply with these terms.
THE WORK IS PROVIDED “AS IS.” McGRAW-HILL AND ITS LICENSORS MAKE NO GUARANTEES OR WARRANTIES AS
TO THE ACCURACY, ADEQUACY OR COMPLETENESS OF OR RESULTS TO BE OBTAINED FROM USING THE WORK,
INCLUDING ANY INFORMATION THAT CAN BE ACCESSED THROUGH THE WORK VIA HYPERLINK OR OTHERWISE,
AND EXPRESSLY DISCLAIM ANY WARRANTY, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO IMPLIED
WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. McGraw-Hill and its licensors do not
warrant or guarantee that the functions contained in the work will meet your requirements or that its operation will be uninterrupted
or error free. Neither McGraw-Hill nor its licensors shall be liable to you or anyone else for any inaccuracy, error or omission, regard-
less of cause, in the work or for any damages resulting therefrom. McGraw-Hill has no responsibility for the content of any informa-
tion accessed through the work. Under no circumstances shall McGraw-Hill and/or its licensors be liable for any indirect, incidental,
special, punitive, consequential or similar damages that result from the use of or inability to use the work, even if any of them has been
advised of the possibility of such damages. This limitation of liability shall apply to any claim or cause whatsoever whether such claim
or cause arises in contract, tort or otherwise.
DOI: 10.1036/0072258098
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
We hope you enjoy this
McGraw-Hill eBook! If
you’d like more information about this book,
its author, or related books and websites,
please click here.
Professional
Want to learn more?
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
Dedication
To Amy, Marissa, and Shaylee
—DF
To —C, >^..^< and >( 8*=
—AB
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
About the Authors
In the daytime Dave Field is a mild-mannered systems engineer. In this role he
has directed the installation of entire network infrastructures at Camp Snoopy in
the Mall of America using technologies such as Active Directory, Microsoft
Exchange, and Microsoft SQL Server. He has been the principal architect of point-
of-sale implementations, ERP roll-outs, and e-commerce initiatives.
After hours Dave becomes an author, freelance trainer, and presenter. A certified
MCSA and MCSE, Dave is expert at networking technologies and support desk
topics. He has delivered training at Microsoft Certified Technical Education Centers
and has authored content for Microsoft and McGraw-Hill/Osborne for the MCSE,
MCSA, and MCDST certifications.
By day, Andrew Brandt works for a major, metropolitan technology monthly.
He is a Senior Associate Editor for PC World, where he covers the security beat,
writes his monthly Privacy Watch column, and writes and edits numerous feature
articles, news stories, and product reviews. His work has earned him awards from
the American Society of Business Press Editors, the Western Publication’s Association,
and American Business Media.
By night, Andrew blogs, codes, and fights crime like all true geeks, in online
games. In his spare moments, he operates Amishrabbit.com, a blog site named for
an over-the-top PR gimmick that dates back to the dot-com boom era. He’s also
a prolific science and technology pundit, and acts as spokeshuman for Bunbun, the
rabbit-in-residence at Amishrabbit. He’s a part-time audio technician for Rocketwars,
an Unreal 2004 mod based on the classic Segasoft game, Rocket Jockey, and he
teaches pottery on Saturday afternoons. You may have also seen him playing such
games as Tribes Football, Planetside, Battlefield 1942, and Tribes: Vengeance, where
he uses the nom de guerre Spike.
About the Technical Editor
Jon L. Jacobi is a freelance technology writer, long-time PC World and CNET
contributor, and software/human interface consultant. When not analyzing storage
industry products or other techno-toys, he plays baseball, indulges in cross-country
drives with the top down, and plays the guitar—well.
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
Contents at a Glance
PART I Set Up Your Home Network
1
Learn about Home Networks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
2
Design Your Own Home Network . . . . . . . . . . . . . . . . . . . . . . . . . . 31
3
Install a Wired Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
4
Install a Wireless Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
PART II Shut the Door on Hackers
5
Keep Your Internet Connections Secure . . . . . . . . . . . . . . . . . . . . . . 107
6
Secure Your Wireless Networks . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
7
Keep Your Systems Secure with System Updates . . . . . . . . . . . . . . . 169
8
Set Up an Effective Antivirus Solution . . . . . . . . . . . . . . . . . . . . . . . 195
PART III Communicate Securely
9
Fight the Junk E-Mail Plague . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
10
Chat and Send Instant Messages Safely . . . . . . . . . . . . . . . . . . . . . . 263
11
Shop and Socialize Securely . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 293
12
Prevent Identity Theft and Protect Yourself . . . . . . . . . . . . . . . . . . . 315
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 339
vii
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
This page intentionally left blank
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
Contents
Foreword . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . xv
Acknowledgments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . xvii
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . xix
PART I
Set Up Your Home Network
CHAPTER 1
Learn about Home Networks . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
Learn What a Home Network Is . . . . . . . . . . . . . . . . . . . . . . . . . . 4
A Quick Visual Tour of a Home Network . . . . . . . . . . . . . . . . . . . 5
The Network You Don’t See . . . . . . . . . . . . . . . . . . . . . . . . 7
Connect Computers and More with Your Network . . . . . . . . . . . . 8
The Role of the Internet . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
Other Uses in the Home . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
Home Networking Challenges . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
Cutting Network Cost . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
Reducing Network Complexity . . . . . . . . . . . . . . . . . . . . . 13
Components of a Network in More Detail . . . . . . . . . . . . . . . . . . 14
The Three Types of Modems You’ll Find Today . . . . . . . . 14
Network Concentrators: The Heart of a Network . . . . . . . . 16
Tie It All Together with Cables and Connectors . . . . . . . . . 19
Use Your Electrical or Telephone Cabling for Data . . . . . . 27
CHAPTER 2
Design Your Own Home Network . . . . . . . . . . . . . . . . . . . . . . . . 31
Determine Your Requirements . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
List Your Computers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
List Your Other Network Devices . . . . . . . . . . . . . . . . . . . . 35
Plan for Future Expansions . . . . . . . . . . . . . . . . . . . . . . . . . 35
Select the Best Network Type for Your Home . . . . . . . . . . . . . . . 36
Planning Cable Routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Why Building Materials Matter . . . . . . . . . . . . . . . . . . . . . 37
Security Implications for Network Selection . . . . . . . . . . . 38
Distance Criteria in Network Selection . . . . . . . . . . . . . . . 38
When You Feel the Need for Speed . . . . . . . . . . . . . . . . . . 38
ix
For more information about this title, click here
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
Create a Physical Map of Your Network . . . . . . . . . . . . . . . . . . . . 39
Sketch the Outline . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Add Your Devices to the Map . . . . . . . . . . . . . . . . . . . . . . . 40
Get the Numbers Right . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
Visualize Your Signal . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
Create a Logical Map of Your Network . . . . . . . . . . . . . . . . . . . . 45
Determine the Placement of Concentrators . . . . . . . . . . . . 45
Create a Network Utilization Plan . . . . . . . . . . . . . . . . . . . . . . . . . 47
CHAPTER 3
Install a Wired Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
Install Your Network Cabling . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
Select Your Installation Tools . . . . . . . . . . . . . . . . . . . . . . . 50
Cable Pulling Techniques . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Connect the Cable Ends . . . . . . . . . . . . . . . . . . . . . . . . . . . 60
When You Just Can’t Get a Cable There . . . . . . . . . . . . . . 61
Connect Your Networking Equipment . . . . . . . . . . . . . . . . . . . . . . 62
Configure Your Computers for Home Networking . . . . . . . . . . . . 63
Manage TCP/IP Addressing . . . . . . . . . . . . . . . . . . . . . . . . 63
Set Up Workgroup Networking . . . . . . . . . . . . . . . . . . . . . 70
Share Your Files and Printers . . . . . . . . . . . . . . . . . . . . . . . 71
Connect Your Network to the Internet . . . . . . . . . . . . . . . . . . . . . . 76
Configure and Share a Direct Internet Connection . . . . . . . 76
CHAPTER 4
Install a Wireless Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
Select the Proper Wireless Ethernet Equipment . . . . . . . . . . . . . . 80
Choose the Device Types for Your Home Network . . . . . . 80
Choose Your Wireless Ethernet Protocol . . . . . . . . . . . . . . 83
Place Your Wireless Network Devices
for Best Reception . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Sources of Radio Interference . . . . . . . . . . . . . . . . . . . . . . . 85
Causes of Signal Attenuation . . . . . . . . . . . . . . . . . . . . . . . 85
Strategies for Extending Signal Range . . . . . . . . . . . . . . . . 86
Configure Your Wireless Network Devices . . . . . . . . . . . . . . . . . . 86
Find a Clear Channel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Configuring a Service Set ID (SSID) . . . . . . . . . . . . . . . . . 88
Enabling Encryption . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
Connect Your Wireless Network to the Internet . . . . . . . . . . . . . . 89
Configure Your Internet Gateway . . . . . . . . . . . . . . . . . . . . 90
Going Online Without a Gateway . . . . . . . . . . . . . . . . . . . . 92
Configure Your Computers for Home Networking . . . . . . . . . . . . 94
Manage TCP/IP Addressing . . . . . . . . . . . . . . . . . . . . . . . . 94
Set Up Workgroup Networking . . . . . . . . . . . . . . . . . . . . . 99
Share Your Files and Printers . . . . . . . . . . . . . . . . . . . . . . . 100
x
How to Do Everything with Windows XP Home Networking
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
PART II
Shut the Door on Hackers
CHAPTER 5
Keep Your Internet Connections Secure . . . . . . . . . . . . . . . . . . . 107
Internet Security Risks for Home Networks . . . . . . . . . . . . . . . . . 108
Attacks by Viruses, Worms, Spies, and Zombies . . . . . . . . 109
Direct Attacks from Internet Sources . . . . . . . . . . . . . . . . . 110
Use Windows XP Security Tools
to Protect Your Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
Manage Your System’s Protection with Windows XP
Security Center (New in SP2) . . . . . . . . . . . . . . . . . . . . . 113
Keep Patched with Updates . . . . . . . . . . . . . . . . . . . . . . . . 116
Protect Your Addresses with Internet
Connection Sharing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
Block Hackers with Windows Firewall . . . . . . . . . . . . . . . . 118
Analyze Your Security with the Microsoft Baseline
Security Analyzer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
Use Third-Party Security Tools
to Protect Your Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 128
Use Antivirus Applications to Stop Viruses . . . . . . . . . . . . 128
Use Antispyware Applications to Terminate Spyware . . . . 129
Use Third-Party Internet Firewalls to Block Hackers . . . . . 132
Evaluate Your Security with Third-Party Auditing Tools . . . 135
Use Defense in Depth to Protect Your Systems . . . . . . . . . . . . . . . 137
Establish a Layered Defense . . . . . . . . . . . . . . . . . . . . . . . . 137
Keep All Systems Up to Date . . . . . . . . . . . . . . . . . . . . . . . 137
CHAPTER 6
Secure Your Wireless Networks . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Cap That Data Gusher You Call a Gateway . . . . . . . . . . . . . . . . . 141
Configure Your Wireless Network for Security . . . . . . . . . . . . . . . 142
Install Your Wireless Hardware with Security in Mind . . . 143
Configure Your Wireless Hardware . . . . . . . . . . . . . . . . . . 146
Keep Your Data Secure over Your Wireless Connections . . . . . . . 156
WiFi Protected Access (WPA) . . . . . . . . . . . . . . . . . . . . . . 156
Wired Equivalent Privacy (WEP) . . . . . . . . . . . . . . . . . . . . 160
Filter MAC Addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
CHAPTER 7
Keep Your Systems Secure with System Updates . . . . . . . . . . . . 169
Why We Patch . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170
Types of Flaws in Computer Programs . . . . . . . . . . . . . . . . 171
The Design/Test/Exploit/Patch/Hack Cycle . . . . . . . . . . . . 174
Use Windows Update to Maintain
Your Operating System Security . . . . . . . . . . . . . . . . . . . . . . . . 175
How Windows Update Works . . . . . . . . . . . . . . . . . . . . . . . 175
Use Internet Explorer to Access Windows Update . . . . . . . 175
Contents
xi
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
xii
How to Do Everything with Windows XP Home Networking
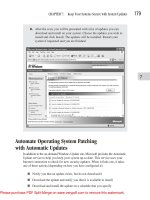
Automate Operating System Patching
with Automatic Updates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
How Automatic Updates Work . . . . . . . . . . . . . . . . . . . . . . 180
Configuring Automatic Updates . . . . . . . . . . . . . . . . . . . . . 180
Maintain Microsoft Applications with Updates . . . . . . . . . . . . . . 183
Locate and Download Updates
for Microsoft Applications . . . . . . . . . . . . . . . . . . . . . . . 183
Use Internet Explorer to Download Office Updates . . . . . . 185
Maintain Non–Microsoft Application Security . . . . . . . . . . . . . . . 190
Locate Security Updates for Non-Microsoft Software . . . . 190
Apply Security Updates for Non-Microsoft Software . . . . 194
CHAPTER 8
Set Up an Effective Antivirus Solution . . . . . . . . . . . . . . . . . . . . 195
The Role of Antivirus Solutions and Services . . . . . . . . . . . . . . . . 196
Viruses, Worms, and Trojan Horses . . . . . . . . . . . . . . . . . . 196
How Antivirus Applications Protect Your System . . . . . . . 199
Choose an Antivirus Solution . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
Antivirus Solution Ratings . . . . . . . . . . . . . . . . . . . . . . . . . 202
Select the Appropriate Feature Set for Your System . . . . . 202
Trial Versions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 203
Other Antivirus Solution Purchase Options . . . . . . . . . . . . 207
Install and Configure Your Antivirus Application . . . . . . . . . . . . . 209
Initial Installation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 209
Operate and Maintain Your Antivirus Solution . . . . . . . . . . . . . . . 225
Perform Manual Virus Sweeps When
You Suspect Malicious Activity . . . . . . . . . . . . . . . . . . . 225
React to Virus Outbreaks with Manual Updates . . . . . . . . . 226
What to Do When You Find a Live Virus . . . . . . . . . . . . . . 226
What to Do When You Suspect a Virus . . . . . . . . . . . . . . . 227
PART III
Communicate Securely
CHAPTER 9
Fight the Junk E-Mail Plague . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
Put an End to Your Spam Problem . . . . . . . . . . . . . . . . . . . . . . . . 232
Defend Your Inbox, Lest You Drown in Spam . . . . . . . . . . 232
Fight Spam on Your Terms, on Your Turf . . . . . . . . . . . . . . . . . . . 233
Avoid Getting Spam in the First Place . . . . . . . . . . . . . . . . . . . . . . 233
Develop Habits That Will Protect Your E-Mail Address . . . 234
Skip Online Activities That Make You More Likely
to Get Spam . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 235
Ditch Your Extremely Spammy Identity . . . . . . . . . . . . . . 236
Filter Spam on Your PC . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 236
Try the Software That’s Free,
or That You’ve Already Got . . . . . . . . . . . . . . . . . . . . . . 237
Shop Around for a Good Spam Filter . . . . . . . . . . . . . . . . . 240
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
Contents
xiii
Get Started with Cloudmark’s SpamNet . . . . . . . . . . . . . . . 241
Install and Run Sunbelt Software’s iHateSpam . . . . . . . . . 244
Get Rid of Spam with Less Effort . . . . . . . . . . . . . . . . . . . . . . . . . 249
Let Your ISP Filter Your Mail for You . . . . . . . . . . . . . . . . 249
Report Spam to the Authorities . . . . . . . . . . . . . . . . . . . . . 251
Spam Fighting Looks Toward the Future . . . . . . . . . . . . . . . . . . . 256
Antispam Legislation Gets Tough . . . . . . . . . . . . . . . . . . . . 256
Spam Fighters Take Legal Action . . . . . . . . . . . . . . . . . . . . 257
Spammers Turn Up the Heat, and Fight Back . . . . . . . . . . 258
CHAPTER 10
Chat and Send Instant Messages Safely . . . . . . . . . . . . . . . . . . . 263
Use Instant Messaging and Chat Wisely . . . . . . . . . . . . . . . . . . . . 264
Evaluate the Risk IM and IRC Pose to You . . . . . . . . . . . . 265
Determine Whether the Risk of Chatting
Is Worth the Benefits . . . . . . . . . . . . . . . . . . . . . . . . . . . . 265
Secure Your Instant Messaging (IM)
and Chat Applications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 266
Get an IM or Chat Client Application . . . . . . . . . . . . . . . . . 266
Stop Viruses, Trojans, and Worms . . . . . . . . . . . . . . . . . . . 270
Prevent Spim from Reaching Your IM Buddy List . . . . . . . 275
Update Your IM Client when New Software is Available . . . 277
Preserve Your IM Settings, Contact Lists,
and Conversation Logs . . . . . . . . . . . . . . . . . . . . . . . . . . 279
Defend Your Privacy in Chat and IM . . . . . . . . . . . . . . . . . . . . . . 281
Who Wants Your Name? . . . . . . . . . . . . . . . . . . . . . . . . . . . 282
Apply Common Sense Liberally . . . . . . . . . . . . . . . . . . . . . 283
Handle Chat and IM Security Issues . . . . . . . . . . . . . . . . . . . . . . . 285
Avoid Chat- and IM-Borne Malware . . . . . . . . . . . . . . . . . 285
Prevent Stalking and Threats in Chat and IM . . . . . . . . . . . 291
CHAPTER 11
Shop and Socialize Securely . . . . . . . . . . . . . . . . . . . . . . . . . . . . 293
Shop Online Safely . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 294
Verify Security Before You Shop . . . . . . . . . . . . . . . . . . . . 294
Read and Understand Web Site Privacy Policy Legalese . . . 301
Protect Your Credit Cards Online . . . . . . . . . . . . . . . . . . . . 307
Safely Socialize Online . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 309
Rules of the Road for Social Networks . . . . . . . . . . . . . . . . 310
Maintain Your Privacy While Job Hunting . . . . . . . . . . . . . . . . . . 311
Know Your Résumé Site . . . . . . . . . . . . . . . . . . . . . . . . . . . 311
Dos and Don’ts for Self-Hosted Résumés . . . . . . . . . . . . . 313
CHAPTER 12
Prevent Identity Theft and Protect Yourself . . . . . . . . . . . . . . . . 315
Keep Identity Thieves Away from Your Data . . . . . . . . . . . . . . . . 316
Safeguard Your Information Before Thieves Strike . . . . . . 317
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
Terminate an Identity Theft Case . . . . . . . . . . . . . . . . . . . . . . . . . 325
Protect Your Identity if Fraud Hits Your Accounts . . . . . . . 325
Protect Your Sensitive Data Online
and on Your PC . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 329
Keep Private Information about Yourself to Yourself . . . . . 329
Perform “Vanity Searches” and Unlist Yourself . . . . . . . . . 330
Steer Clear of Phishing Scams . . . . . . . . . . . . . . . . . . . . . . 333
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 339
xiv
How to Do Everything with Windows XP Home Networking
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
Foreword
Windows XP has evolved from more than a decade of continued windows
development. During this time, Microsoft has been committed to understanding
and meeting the diverse needs of its customers, and XP is a truly usable operating
system with unsurpassed functionality. Windows XP is the foremost desktop operating
system all over the world. If one thing is missing though, it would be proper security.
One of the most common things I hear from government and industry leaders is
that there needs to be clear guidance, especially security guidance, for home and
small office users for their PCs. By the time this book is printed, XP Service Pack 2
will be released and that will be a major step to meet the needs of Microsoft’s
customers to make their lives better, safer, and their work easier.
David Field proposed a textbook to Osborne to cover Internet security topics
including anti-virus, personal firewalls, spam, and spyware. The original concept
for the book was to be all security. Upon further reflection, Osborne felt readers
wanted a broader coverage, covering topics such as home networking. The
Windows XP operating system easily adapts to most networking solutions, but it
helps to have a design or recipe showing technologies and tools such as wireless,
cable, and DSL modems.
Andy Brandt from PC World joined the project to help make the book richer
than just security, to be a real how-to for home and small-office users. Andy adds
tremendous enthusiasm and knowledge to the project also, and the combination is
a great team.
I’d like to extend congratulations to David and Andy for producing a truly useful
book, a book that goes beyond telling the reader about things, but one that tells the
reader how to do things. This book is an invaluable resource for both beginners
and computing professionals and all levels in between. There’s no better guide for
learning and mastering how to put Windows XP to work. It will be another fine
book in Osborne’s “How to do Everything” series.
xv
Copyright © 2004 by McGraw-Hill Companies. Click here for terms of use.
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
What this has evolved into is 12 chapters ranging from anti-spyware to wiring
the walls to privacy and identity protection. The chapters are written in a modular
fashion—the information you need is right there, so you don’t have to keep skipping
around. The book was written to the soon-to-be-released Service Pack 2, so it will
be up to date for more than a year.
This is a book that will find a place within arms reach of your computer. I’ve
been using Windows operating systems since Windows 3.1 and XP is by far my
favorite; everything is intuitive. This book will help you get the most out of your
computer, and serves a real need. Make sure you read it and don’t just put it on
the shelf!
Essentially yours,
Stephen Northcutt,
Director of Training and Certification
The SANS Institute
August 2004
xvi
How to Do Everything with Windows XP Home Networking
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
Acknowledgments
Let me begin by thanking the ones who helped me the most with this work. Without
the encouragement, support, and tolerance of my wife and girls, I would not have
been able to do this. They inspire me to do the best job I can and find me the time
to do it.
To Megg, Agatha, Julie, Carolyn, Jody, Bob, and the others at Osborne: Thanks
for helping us shape this work into something we can all learn from. Thanks to my
co-author Andy Brandt for his advice, assistance, and especially his contacts.
Thanks to Jon Jacobi of PC World for keeping our facts straight and to Bob Hillery
of IntelGuardians for lending his voice to our work. Thanks, Stephen Northcutt of
Sans Institute for your time and encouragement. Finally, thanks to Laura, Stacey,
Sherry, Jackie, Katrina, and the others at Studio B for letting me keep writing on
my mind.
—Dave Field
I’ve got to thank Clare, not only for tolerating extended late-night writing
sessions, but for doing a hundred different supportive things a day, and for being
the supra-genius editor-writer-designer that she is. I’d also like to thank PC World
for paying me to do, and write about, some of the fun, offbeat technology stuff I
also happen to love.
My editors at OMH have been a terrific source of insight and a fount of ideas
for which I’m grateful. I also want to thank Bob Garza for giving me a shove into
the world of tech books (and indoor skydiving), and Dave Field for being such
a networking mensch. Michael Lasky let me put sample chapters on the PC World
cover disc, fulfilled my incessant battery requests, and repeatedly told me my
second-favorite joke, which still makes me smile.
xvii
Copyright © 2004 by McGraw-Hill Companies. Click here for terms of use.
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.
Finally, I’ve got a huge list of family, friends, and Internet acquaintances to
thank, not only for their support and enthusiasm over this project, but also for
putting up with my absence while I spent my every waking moment working on
this book. I can’t name every one of you, just out of the environmental considerations
of using all that ink, but you know who you are. I owe each of you a cookie
(or, depending on what species you are, a carrot).
—Andrew Brandt
xviii
How to Do Everything with Windows XP Home Networking
Please purchase PDF Split-Merge on www.verypdf.com to remove this watermark.